ExtremeCloud IQ Site Engine includes ten system-defined ExtremeControl profiles that define the authorization and assessment requirements for the end-systems connecting to the network.
The system-defined profiles are:
- Administrator
- Allow
- Default
- Guest Access
- Notification
- Pass Through
- Quarantine
- Registration Denied Access
- Secure Guest Access
- Unregistered
Use the Access Control Profiles window to view and edit these profiles, and define new profiles if desired. Any changes made in this window are written immediately to the ExtremeCloud IQ Site Engine database.
To open the Access Control Profiles window, navigate to the Access Control tab and select the ExtremeControl Profiles tab in the left-panel.
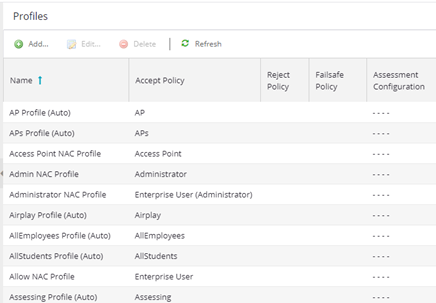
The window includes the following buttons and functionality:
- Add Button

- Use this button to open the New ExtremeControl Profile window, where you can add an ExtremeControl profile.
- Edit Button
- Use this button to open the Edit ExtremeControl Profile window, where you can edit an existing ExtremeControl profile.
The Access Control Profiles table includes the following columns:
- Accept Policy
- The Accept policy defined for this profile. An Accept policy is
applied to an end-system when
- an end-system has been authorized locally by the ExtremeControl engine and has passed an assessment (if assessment in enabled).
- authentication is configured to replace the attributes returned from the RADIUS server with the Accept policy.
-
If your Accept policy is "Use User/Host LDAP Policy Mappings," an Accept Policy will be assigned, based on the end-system information in the LDAP database and the LDAP Policy Mappings configured in the Authentication Mapping.
-
Authenticated Guest and IoT Management provisioners cannot match a rule associated with an Accept Policy = -- No Policy --. Guest and IoT Management authenticated provisioners must match a rule in Control, mapped to an Accept Policy that is not mapped to "-- No Policy --“.
| NOTES: |
|
|---|
- Failsafe Policy
- The Failsafe policy defined for this profile. A Failsafe policy is applied to an end-system if the end-system's IP address cannot be determined from its MAC address, or if there has been a scanning error and a scan of the end-system could not take place.
- Assessment Configuration
- The assessment configuration defined for this profile. The configuration define the assessment requirements for end-systems
- Assessment Interval
- If assessment is required, this defines the interval between required assessments for an end-system.
- Quarantine Policy
- The Quarantine policy defined for this profile. A Quarantine policy is applied to an end-system if the end-system fails an assessment.
- Assessment Policy
- The Assessment policy defined for this profile. An Assessment policy is applied to an end-system while it is being assessed.
- Hide Assessment/Remediation Details
- Denotes whether the option to hide assessment or remediation information on the Remediation Web Page has been selected.
For information on related help topics: