ExtremeCloud IQ Site Engine
24.02.12 Release Notes
A PDF copy of these release notes can be found here.
ExtremeCloud IQ Site Engine includes all the features and functionality of Extreme Management Center as well as issues that have been resolved and configuration changes for this release.
If you are an existing Extreme Management Center customer, contact your representative to have your Extreme Management Center license migrated to an ExtremeCloud IQ Site Engine license. The ExtremeCloud IQ Site Engine license also includes licensing for ExtremeAnalytics.
| IMPORTANT: |
|
For information regarding the features supported by specific devices, see the Firmware Support Matrix. Version 24.02.12 of ExtremeCloud IQ Site Engine supports the devices listed in the matrix.
Devices that do not have serial numbers or MAC addresses in Extreme Management Center must be rediscovered after you upgrade to ExtremeCloud IQ Site Engine before they can be onboarded to ExtremeCloud IQ.
Connected mode only - If your number of devices exceeds your licenses available, ExtremeCloud IQ Site Engine transitions to a license violation state and your access to ExtremeCloud IQ Site Engine is locked. To resolve the license shortage you need to access the Extreme Networks portal or ExtremeCloud IQ to evaluate the quantities of available Pilot and Navigator licenses versus the number of licenses required by ExtremeCloud IQ Site Engine.
Licensing Changes
Starting in ExtremeCloud IQ Site Engine version 23.2.10 each stack member consumes a license in connected mode. In connected mode, ExtremeCloud IQ Site Engine now reports stack members to ExtremeCloud IQ. If you use stacks in connected mode, ensure that enough ExtremeCloud IQ Pilot licenses are in the license pool before upgrading to ExtremeCloud IQ Site Engine 23.2.10 or later.
Beginning with ExtremeCloud IQ Site Engine version 21.04.10, your ExtremeAnalytics license is included as part of your ExtremeCloud IQ Pilot license. Separate licenses are no longer required.
For users upgrading from Extreme Management Center to ExtremeCloud IQ Site Engine, note that the XIQ-NAC subscription must be used instead of IA-ES- license. For new users that complete an initial install of ExtremeCloud IQ Site Engine, ExtremeControl licensing does not include end-system capabilities.
End of Software Maintenance
In ExtremeCloud IQ Site Engine version 23.7.13 and after, the following components and features are at end-of-software maintenance:
-
Guest and IoT Manager - last version is 23.7.11.6
-
Fabric Manager - last version is 22.9.13.5
-
Posture Assessment (both the agent-based and agent-less)
Onboarding ExtremeCloud IQ Site Engine to ExtremeCloud IQ in Connected Deployment Mode
After installing or upgrading to ExtremeCloud IQ Site Engine, you need to onboard ExtremeCloud IQ Site Engine to ExtremeCloud IQ. When the onboarding is complete, you can then access ExtremeCloud IQ Site Engine.
Entering your ExtremeCloud IQ name and password are required during the first-time login to ExtremeCloud IQ Site Engine.
| NOTE: | If Extreme Management Center is onboarded to ExtremeCloud IQ, when you upgrade to ExtremeCloud IQ Site Engine, you need to remove Extreme Management Center from ExtremeCloud IQ before onboarding ExtremeCloud IQ Site Engine. |
Enhancements
The following enhancements were made to ExtremeCloud IQ Site Engine in this release. For additional information about each of the enhancements listed in the release notes, see ExtremeCloud IQ Site Engine Documentation .
ExtremeCloud IQ Site Engine
|
Changed the location and URL for Analytics Fingerprint update. Verify your firewall rules to allow communication from ExtremeCloud IQ Site Engine to http://xiqse.extremenetworks.com. Authentication is not mandatory, predefined credentials are cleared on upgrade. |
Customer Found Defects and Known Issues
Customer Found Defects Addressed 24.02.12
| ExtremeCloud IQ Site Engine CFDs Addressed | ID |
|---|---|
| Disk expansion on medium and large hyper-v installations will now work regardless of disk ordering. | 02779533 02820493 02823796 02921583 |
| Local mirror appliance upgrades from ubuntu 18.04 to ubuntu 20.04 will disable all proxy settings before running the upgrade, and restore them when the upgrade has finished. | 02818322 |
|
ExtremeManagement CFDs Addressed |
ID |
|---|---|
|
When moving a device from one site to another site, now the site archives are also updated. |
02829219 |
| Map drawings and labels should no longer be removed when a map is edited. | 02856784 |
| EXOS/Switch Engine will no longer report failed when a save config operation takes longer than expected. | 02931367 |
Customer Found Defects Addressed 24.02.11
| ExtremeControl CFDs Addressed | ID |
|---|---|
| Addressed an issue with Entra IDs not included in a NAC database backup. Now added the Entra ID database to the NAC database backup. | 02915773 |
| Addressed an issue when Access Control Engine timed out while connecting to ExtremeCloud IQ Site Engine over connections with higher latency. Now increased the JMS connection timeout to 60 seconds. | 02924621 |
Customer Found Defects Addressed 24.02.10
| ExtremeCloud IQ Site Engine CFDs Addressed | ID |
|---|---|
| Addressed an issue with the Securities Best Practices documentation to fix technical errors. Now the Rev AB from February 2024 is the corrected updated version. | 02761167 |
| ExtremeControl CFDs Addressed | ID |
|---|---|
| Addressed an issue with importing MACs to End-System Groups not working for users who logged in with @ sign in username. | 02776741 |
| Address an issue with certain EAP-TLS clients unable to authenticate because the EAP start packet contained the length field. Now the length is not configured by default for EAP-TLS unfragmented packets. | 02829369 02852238 02862459 |
| Addressed an issue by adding a new option in Administration> Options> Access Control> Data Persistence> End-Systems Search Criteria to include/exclude the MAC OUI Vendor from searching in the end-systems table. | 02832682 |
| Addressed an issue with being unable to update AAA Trusted Authorities if CA Certificate contained a private key. Now a CA cert with a private key can be added to the trusted store. | 02856204 |
| Addressed an issue when there was multiple LDAP(S) URLs configured, the first URL was always used for SSL connection configuration which was incorrect. Now can use the correct URL for LDAP configuration. | 02894783 |
| ExtremeManagement CFDs Addressed | ID |
|---|---|
| Addressed an issued with an Extreme Connect Module Sync Delay sleep timer calculation on the number of End-Systems when there are more than 1000 End-Systems. You can now override the sleep timer if there are more than 1000 End-Systems. | 02808576 |
| Addressed an issue when restoring a template config to a VOSS switch can cause config.cfg to become unreadable. | 02857609 |
| Addressed an issue with an enforce failed error with trunking. The VLAN trunking feature was taking all the VLANS available (including Onboarding VLAN) on the device and applying them to the port. Now the Onboarding VLAN is excluded. | 02864717 |
| Addressed an issue where the Context Menu > More Views > User Sessions, and Fabric L2VSNs options were not greyed out or hidden when not applicable. | 02869173 |
| Addressed an issue where packet loss or a bad TCP connection could prevent a cloud connected system startup. | 02876953 |
Known Issues Addressed in 24.02.12
|
Addressed an issue with Administration > Server > Server Utilities > FlexView Editor / MIB Tools unable to launch due to unsigned Jar files in 24.02.11. |
| Addressed security vulnerabilities by updating the samba version to the latest available in Ubuntu 20.04. |
Known Issues Addressed in 24.02.11
| Addressed a HTTP 404 issue with exporting end-system data when the username contains special characters. |
| Addressed a missing Intune Compliance Module in diagnostics. Intune Compliance Module debugging is now available in official diagnostics. |
Known Issues Addressed in 24.02.10
| Addressed an issue where the SSH configuration> SSH Port field could save an invalid port range causing the SSH daemon to fail on next startup. The SSH Port field is now restricted to values 1 - 65535. |
| Addressed an issue with Phone Number verification in the ExtremeControl Captive Portal for various languages. |
| Addressed an issue with the "updateServiceDefinition" GraphQL (NBI) API call when no VRF ID is provided then the default VRF ID (-1) is used. |
| Addressed an issue with the "deletePolicyMappingEntry" GraphQL (NBI) API call failing as in use. |
| Addressed an issue where ExtremeCloud IQ connected ping only devices did not have a valid uptime shown in ExtremeCloud IQ Site Engine. |
| Addressed an issue where if you selected multiple VOSS/Fabric Engine devices and select the Configure button, if the devices had different SPBM Nicknames or DvR settings then the configuration did not save properly in the GUI. |
| Addressed an issue where if you configured Fabric Connect values for multiple devices simultaneously with the right-click configure, followed by multiple selections, that could cause the data to be copied from one device to another. |
| Addressed an issue where the SSH configuration> SSH Port field could save an invalid port range causing the SSH daemon to fail on next startup. The SSH Port field is now restricted to values 1 - 65535. |
| Addressed an issue of an unmanaged device allowing FlexView. FlexViews are supported on managed devices only. |
| Addressed an issue with ZTP+ Onboarding using pre-registered device the Fabric Connect services were not shown. |
| Addressed an issue when the wrong hostname of the neighbor could be reported in the port tree and reported to ExtremeCloud IQ. |
| Addressed an issue where the SSH configuration> SSH Port field could save an invalid port range causing the SSH daemon to fail on next startup. The SSH Port field is now restricted to values 1 - 65535. |
Addressed Vulnerabilities
This section presents the vulnerabilities reported by vulnerability scanners in previous versions. The following components received updates in 24.02 regardless of whether the vulnerability could have been exploited or not. If you need more information on vulnerability testing, see Security and Vulnerability Testing.
24.02.12 ExtremeAnalytics and Application Analytics Traffic Sensor images:
CVE-2022-48624, CVE-2024-24806, CVE-2023-50868, CVE-2023-5517, CVE-2023-6516, CVE-2023-4408, CVE-2023-50387, CVE-2024-26130, CVE-2023-50782, CVE-2021-3995, CVE-2021-3996, CVE-2024-22667, CVE-2023-22995, CVE-2023-51780, CVE-2021-44879, CVE-2023-51782, CVE-2024-0340, CVE-2023-6121, CVE-2023-4244, CVE-2023-51779, CVE-2021-30535, CVE-2023-23004, CVE-2024-24855, CVE-2023-23000, CVE-2024-1086, CVE-2023-4641, CVE-2021-33560, CVE-2021-40528
24.02.12 ExtremeControl images:
CVE-2022-48624, CVE-2024-24806, CVE-2023-50868, CVE-2023-5517, CVE-2023-6516, CVE-2023-4408, CVE-2023-50387, CVE-2024-26130, CVE-2023-50782, CVE-2021-3995, CVE-2021-3996, CVE-2024-22667, CVE-2023-22995, CVE-2023-51780, CVE-2021-44879, CVE-2023-51782, CVE-2024-0340, CVE-2023-6121, CVE-2023-4244, CVE-2023-51779, CVE-2021-30535, CVE-2023-23004, CVE-2024-24855, CVE-2023-23000, CVE-2024-1086, CVE-2023-4641, CVE-2021-33560, CVE-2021-40528, CVE-2023-3823, CVE-2023-3824, CVE-2024-0985, CVE-2017-1000211, CVE-2016-9179, CVE-2021-38165
24.02.12 ExtremeCloud IQ Site Engine images:
CVE-2022-48624, CVE-2024-24806, CVE-2023-50868, CVE-2023-5517, CVE-2023-6516, CVE-2023-4408, CVE-2023-50387, CVE-2024-26130, CVE-2023-50782, CVE-2021-3995, CVE-2021-3996, CVE-2024-22667, CVE-2023-22995, CVE-2023-51780, CVE-2021-44879, CVE-2023-51782, CVE-2024-0340, CVE-2023-6121, CVE-2023-4244, CVE-2023-51779, CVE-2021-30535, CVE-2023-23004, CVE-2024-24855, CVE-2023-23000, CVE-2024-1086, CVE-2023-4641, CVE-2021-33560, CVE-2021-40528, CVE-2020-26572, CVE-2020-26571, CVE-2020-26570, CVE-2019-15946, CVE-2019-15945
24.02.11 ExtremeCloud IQ Site Engine, ExtremeAnalytics, ExtremeControl, and Application Analytics Traffic Sensor images:
CVE-2024-25062, CVE-2024-0727, CVE-2023-6932, CVE-2023-6931, CVE-2023-6606, CVE-2023-6516, CVE-2023-6277, CVE-2023-6237, CVE-2023-6228, CVE-2023-6129, CVE-2023-6040, CVE-2023-5678, CVE-2023-5517, CVE-2023-52356, CVE-2023-51764, CVE-2023-50868, CVE-2023-50387, CVE-2023-46343, CVE-2023-45863, CVE-2023-4408, CVE-2023-43040, CVE-2023-3817, CVE-2023-35827, CVE-2023-3446, CVE-2023-34324, CVE-2023-32681, CVE-2023-2953, CVE-2023-28450, CVE-2022-48065, CVE-2022-48063, CVE-2022-47695, CVE-2022-40897, CVE-2022-2806, CVE-2022-24407, CVE-2021-4122
24.02.10 ExtremeCloud IQ Site Engine, ExtremeAnalytics, ExtremeControl, and Application Analytics Traffic Sensor images:
CVE-2017-6363, CVE-2020-13645, CVE-2020-14367, CVE-2020-15704, CVE-2020-15709, CVE-2020-16121, CVE-2020-16122, CVE-2020-25219, CVE-2020-26154, CVE-2020-27350, CVE-2020-27351, CVE-2020-28241, CVE-2020-3810, CVE-2020-8252, CVE-2020-8927, CVE-2021-22918, CVE-2021-24031, CVE-2021-24032, CVE-2021-38115, CVE-2021-40145, CVE-2021-40153, CVE-2021-41072, CVE-2021-41617, CVE-2022-39348, CVE-2022-44840, CVE-2022-45703, CVE-2022-46908, CVE-2022-47007, CVE-2022-47008, CVE-2022-47010, CVE-2022-47011, CVE-2023-46137, CVE-2023-50164, CVE-2023-51384, CVE-2023-51385, CVE-2023-51764, CVE-2023-6004, CVE-2023-6918, CVE-2023-7104, CVE-2024-0553, CVE-2024-0567, CVE-2024-20918, CVE-2024-20919, CVE-2024-20921, CVE-2024-20922, CVE-2024-20923, CVE-2024-20925, CVE-2024-20926, CVE-2024-20945, CVE-2024-20952, CVE-2024-22365
Installation, Upgrade, and Configuration Changes
Installation Information
There are three tiers of licenses for ExtremeCloud IQ Site Engine and devices:
- Pilot
- Navigator
- No License
As you begin to onboard ExtremeCloud IQ Site Engine and your devices, ExtremeCloud IQ will determine if you meet or exceed the license limits for each license type.
For complete installation instructions, see ExtremeCloud IQ Site Engine Suite Installation.
| IMPORTANT: | The Compliance tab is available and supported by Extreme on an engine running the Linux operating system supplied by Extreme. Other Linux operating systems can support ExtremeCompliance functionality, but python version 2.7 or higher must be installed. Additionally ExtremeCompliance functionality requires the git, python2, python mysql module, python setuptools module, and python "pygtail" module packages be installed and related dependencies managed by the customer for their server’s unique operating system and version. |
Upgrading Without an Internet Connection
!!! ATTENTION !!!
We can attempt to upgrade the OS without using the internet if there were no extra Ubuntu packages installed. If there were extraneous packages installed, the upgrade will fail with this method.
Do you want to attempt a local in-place upgrade of the OS and reboot when complete? (Y/n)Custom FlexViews
When reinstalling ExtremeCloud IQ Site Engine Console, the installation program saves copies of any FlexViews you created or modified in the <install directory>\.installer\backup\current\appdata\System\FlexViews folder.
If you are deploying FlexViews via the ExtremeCloud IQ Site Engine server, save them in the appdata\VendorProfiles\Stage\MyVendorProfile\FlexViews\My FlexViews folder.
Custom MIBs and Images
If you are deploying MIBs via the ExtremeCloud IQ Site Engine server, they are saved in the appdata\VendorProfiles\Stage\MyVendorProfile\MIBs\ folder.
If you are deploying device images (pictures) via the ExtremeCloud IQ Site Engine server, they are saved in the appdata\VendorProfiles\Stage\MyVendorProfile\Images\ folder.
Important Upgrade Information
ExtremeCloud IQ Site Engine version 24.02.12 supports upgrades from Extreme Management Center 8.5.7 or ExtremeCloud IQ Site Engine 23.4.12 only. The following table details the upgrade path supported for each NetSight, Extreme Management Center or ExtremeCloud IQ Site Engine version.
| NOTE: |
ExtremeCloud IQ Site Engine Version 24.02.12 contains an OS upgrade. Internet connectivity is required to download custom packages. The installer prompts "Do you want to use the Internet to perform the OS upgrade?". The offline upgrade path is supported when no custom packages are installed (answer N). The online upgrade is required when custom packages are manually installed (answer Y). An online upgrade is recommended when an online upgrade was used previously, however there is a risk of session timeout due to 15 minutes of screen inactivity. To upgrade Access Control Engines and Application Analytics Engines you can use the directive --keepalive to decrease the chance of a session expiry timeout from 15 minutes of no screen activity. |
| From Version (currently running) | To Version (next step in upgrade path) |
|---|---|
| ExtremeCloud IQ Site Engine 23.4.12, 23.7.x, 23.11.x | ExtremeCloud IQ Site Engine 24.02 |
| ExtremeCloud IQ Site Engine 21.x, 22.x, 23.2.x 23.4.10, 23.4.11 | ExtremeCloud IQ Site Engine 23.4.12 |
| Extreme Management Center version 8.5.7 | ExtremeCloud IQ Site Engine 24.02 |
| Extreme Management Center version 8.2.x to 8.5.6 | Extreme Management Center 8.5.7 |
| Extreme Management Center version 8.0.x to 8.1.x | Extreme Management Center 8.3.3.11 |
| NetSight version 7.1.4.1 | Extreme Management Center 8.3.3.11 |
| NetSight version 7.x | NetSight 7.1.4.1 |
| NetSight version 6.3.0.186 | NetSight 7.1.4.1 |
| NetSight version 6.x | NetSight 6.3.0.186 |
| IMPORTANT: | A backup (Administration > Backup/Restore) of the database must be performed prior to the upgrade and saved to a safe location. |
|---|
If you use LDAPS with a Fully Qualified Domain Name (FQDN) in the URL to authorize a user to the OneView, then ExtremeCloud IQ Site Engine presents the Server Certificate (located in Administration > Certificates > Server Certificate Information) to the LDAPS server. If the LDAPS server presents a certificate that does not match the LDAPS URL, then the certificate is rejected with the error “Certificate Unknown”.
The best practice is to use a trusted certificate if the LDAPS URL is defined with FQDN, otherwise the LDAPS server might not accept the LDAPs connection. The alternative option is to use an IP address in the LDAPS URL instead of FQDN.
Important Upgrade Considerations
- If your network is using ExtremeAnalytics or ExtremeControl engines, or another add-on feature, you must first perform the ExtremeCloud IQ Site Engine upgrade to version 24.02.12 and then upgrade the feature.
- To upgrade Traffic Sensor from version 21.x, a fresh installation is recommended. If the fresh installation cannot be used, then please check Knowledge Base for a special procedure.
- If the online upgrade fails due to an Internet connectivity issue, fix the connectivity issue and rerun the upgrade.
| IMPORTANT: | When performing an upgrade, be sure to back up the database prior to performing the upgrade, and save it to a safe location. Use the Administration > Backup/Restore tab to perform the backup. |
- When upgrading the ExtremeCloud IQ Site Engine server, ExtremeAnalyticsengine, or ExtremeControlengine to version 24.02.12, ensure the DNS server IP address is correctly configured.
-
When upgrading to ExtremeCloud IQ Site Engine version 24.02.12, if you adjusted the ExtremeCloud IQ Site Engine memory settings and want them to be saved on upgrade, a flag (
-DcustomMemory) needs to be added to the/usr/local/Extreme_Networks/NetSight/services/nsserver.cfgfile.
For example:-Xms12g -Xmx24g -XX:HeapDumpPath=../../nsdump.hprof -XX:+HeapDumpOnOutOfMemoryError -XX:MetaspaceSize=128m -DcustomMemory
License Renewal
Upgrading to ExtremeCloud IQ Site Engine version 24.02.12 requires you to transition from perpetual to subscription-based license model. Existing NMS licenses do not provide access to ExtremeCloud IQ Site Engine. If your perpetual licenses were not transitioned to subscription-based licenses, contact your Extreme Networks Representative for assistance.
Free Space Consideration
When upgrading to ExtremeCloud IQ Site Engine version 24.02.12, a minimum of 15 GB of free disk space is required on the ExtremeCloud IQ Site Engine server
To increase the amount of free disk space on the ExtremeCloud IQ Site Engine server, perform the following:
- Decrease the number of ExtremeCloud IQ Site Engine backups (by default, saved in the
/usr/local/Extreme_Networks/NetSight/backupdirectory). - Decrease the Data Persistence settings (Administration > Options > Access Control > Data Persistence).
- Remove unnecessary archives (Network > Archives).
-
Delete the files in the
<installation directory>/NetSight/.installerdirectory.
Site Discover Consideration
Discovering devices via the Site tab using a Range, Subnet, or Seed discover might not successfully add all expected devices. To correct the issue, increase the Length of SNMP Timeout value on the Administration > Options > Site tab in the Discover First SNMP Request section.
ExtremeAnalytics Upgrade Information
Enabling or disabling the disk flow export feature might cause enforce operations to time out. Enforcing again resolves the issue.
When you delete an ExtremeXOS/Switch Engine device that is configured as a flow source via the Flow Sources table of the
Analytics > Configuration > Engines > Configuration tab from the Devices list on the Network > Devices tab, an error message is generated in the server.log. The message does not warn you that the device is in use as a flow source. Adding the device back in the Devices list on the Network > Devices tab or removing the device from the Flow Source table fixes the issue.
The Flow Sources table on the Analytics > Configuration > engine > Configuration tab may take a few minutes to load.
ExtremeControl Version 8.0 and later
Beginning in version 8.0, ExtremeControl may fail to join Active Directory when accessing as a Standard Domain User with Descendant Computer Objects ("Reset password" permissions only) group member.
To allow this functionality, add the following permissions:
- Reset Password
- Validated write to DNS host name
- Validated write to service principal
- Read and write account restrictions
- Read and write DNS host name attributes
- Write servicePrincipalName
Other Upgrade Information
Immediately after you install version 24.02.12 on the ExtremeControlengine, the date and time does not properly synchronize and the following error message displays:
WARNING: Unable to synchronize to a NTP server. The time might not be correctly set on this device.
Ignore the error message and the date and time automatically synchronize after a short delay.
Additionally, the following message might display during the ExtremeControl upgrade to version 24.02.12:
No domain specified
To stop domain-specific winbindd process, run /etc/init.d/winbindd stop {example-domain.com}
Upgrading ExtremeControl Engine to Version 24.02.12
General Upgrade Information
The EAP-TLS Certificates with SHA1 are considered weak and are not accepted anymore. The radius server fails to start with the SHA1 certificate. You can use a more secure certificate, such as SHA256.
You are not required to upgrade your ExtremeControl engine version to 24.02.12 when upgrading to ExtremeCloud IQ Site Engine version 24.02.12. However, both ExtremeCloud IQ Site Engine and ExtremeControl engine must be at version 24.02.12 in order to take advantage of the new ExtremeControl version 24.02.12 features. ExtremeCloud IQ Site Engine version 24.02.12 supports managing ExtremeControl engine versions 8.5.7, 21.x, 22.x, 23.x and up to 24.02.12.
In addition, if your ExtremeControl solution utilizes a Nessus assessment server, you should also upgrade your assessment agent adapter to version 24.02.12 if you upgrade to ExtremeControl version 24.02.12.
You can download the latest ExtremeControl engine version at the Extreme Portal.
Agent Version for NAC Agent-Based Assessment - Legacy
If you are using onboard agent-based assessment, be aware that the agent version is upgraded during the ExtremeControl engine software upgrade. If you would like end-systems to update their agent to the new version, you must configure your assessment test set to test for the new agent version. Refer to the Important Upgrade Information section in the ExtremeCloud IQ Site Engine Release Notes or the agent version included in the ExtremeControlengine software.
LDAPS servers with FQDN
If the LDAPS server URL uses a Fully Qualified Domain Name (FQDN), then the LDAPS client of Access Control Engine presents the internal Communication Certificate to the LDAPS server. If the LDAPS server URL uses a FQDN then the LDAPS client of ExtremeCloud IQ Site Engine presents the Server Certificate (located in Administration > Certificates > Server Certificate Information) to the LDAPS server. If the LDAPS server presents a certificate that does not match the LDAPS URL, then the certificate is rejected with the error “Certificate Unknown”
The best practice is to use trusted certificates if the LDAPS URL is defined with FQDN, otherwise the LDAPS server might not accept the LDAPS connection. If the LDAPS server URL uses an IP address then the LDAPS client (of both Access Control Engine and ExtremeCloud IQ Site Engine) does not present the Certificate to the LDAPS server.
Upgrading to Policy Manager 24.02.12
- Policy Manager 24.02.12 only supports ExtremeWireless Controller version 10.51. If you upgrade to ExtremeCloud IQ Site Engine 24.02.12 prior to upgrading your controllers, then Policy Manager does not allow you to open a domain where the controllers already exist or add them to a domain. A dialog is displayed indicating your controllers do not meet minimum version requirements and that they must be upgraded before they can be in a domain.
- Following an upgrade to Wireless Controller version 8.31 and higher, a Policy Manager enforce fails if it includes changes to the default access control or any rules that are set to contain. To allow Policy Manager to modify the default access control or set rules to contain, you must disable the "Allow" action in policy rules contains to the VLAN assigned by the role checkbox accessed from the Wireless Controller's web interface on the Roles > Policy Rules tab. This will allow the enforce operation to succeed.
Fabric Configuration Information
Certificate
Fabric Manager might be unavailable via ExtremeCloud IQ Site Engine after upgrading if the certificate is missing in ExtremeCloud IQ Site Engine Trust store.
To ensure Fabric Manager is available, enter the Fabric Manager certificate in the ExtremeCloud IQ Site Engine Trust store using Generate Certificate option. See Add Fabric Manager Certificate for the certificate procedure.
Authentication Key
When you provision authentication keys for Fabric Attach, the key cannot be read back for security reasons. When the key is read from the device, it always shows "****". For this reason, it might seem that there is a configuration mismatch when one does not exist.
Service Configuration Change
If you change a configured service via the Configure Device window that references one of the following, and then enforce those changes to the device, the configuration on the device might change unexpectedly:
- MLT
- SMLT
- Port-specific settings to a port belonging to an MLT or SMLT
To prevent this merge, change rows in the Enforce Preview window where MLT or SMLT are in use from Current to Desired.
To correct the issue after enforcement, modify the service on the device via the CLI.
CLIP Addresses
Using the CLIP Addresses table in the Configure Device window, you can enter addresses in both IPv4 and IPv6 formats. However, ExtremeCloud IQ Site Engine version 24.02.12 only supports applying a single address (either IPv4 or IPv6) to a Loopback Interface.
Gateway Address Configuration Change
In versions of ExtremeCloud IQ Site Engine prior to 24.02.12, the Default Gateway IP Address is configured as part of the VLAN. In 24.02.12, the Default Gateway IP Address is configured as part of the VRF.
When enforcing VRFs to a device after upgrading to version 24.02.12, merge any Default Gateway IP Addresses from the device into the configuration of ExtremeCloud IQ Site Engine to prevent incorrect configuration of the device.
Upgrading VSP-8600
When upgrading from Extreme Management Center version 8.2 to version 8.3. manually reload previously discovered VSP-8600 devices to gain access to Fabric Connect features.
Removing Fabric Connect Configuration
Removing a device's Fabric Connect configuration by setting the Topology Definition to <None> may fail if the device has Logical Interfaces assigned to ISIS.
Password Configuration
Fabric Manager fails to onboard in ExtremeCloud IQ Site Engine if the root password includes an ampersand (&) character. Additionally, if the Administration > Inventory Manager > SCP tab contains a password that includes an ampersand (&) in ExtremeCloud IQ Site Engine, the Fabric Manager firmware does not download successfully.
Ensure you use a password without an ampersand (&) character.
VRF Configuration
VOSS/Fabric Engine SNMP performance is adversely affected as the number of VRF configurations increases. This issue can be resolved by upgrading toVOSS/Fabric Engine release 8.1.1 or later or VSP-8600 series version 6.3.3 or later.
Device Configuration Information
VDX Device Configuration
To properly discover interfaces and links for VDX devices in ExtremeCloud IQ Site Engine, enable three-tuple-if on the device.
| NOTE: | To enable three-tuple-if on the device in ExtremeCloud IQ Site Engine:
|
Additionally, for ExtremeCloud IQ Site Engine to display VCS fabric , the NOS version must be 7.2.0a or later.
Rediscover VDX devices after upgrading to ExtremeCloud IQ Site Engine.
VOSS/Fabric Engine Device Configuration
Topology links from VOSS/Fabric Engine devices to other VOSS/Fabric Engine or ERS devices might not display in a topology map (or might display inconsistently). To ensure topology map links display correctly, verify that the VOSS/Fabric Engine device is configured to publish its management IP address in the autotopology (SONMP) data.
Ensure that the output of show sys setting command shows:
autotopology : on
ForceTopologyIpFlag : true
clipId-topology-ip : 0
If the output values displayed are different, configure the VOSS/Fabric Engine device to publish management IP address in SONMP data by executing the following CLI commands:
(config)# autotopology
(config)# sys force-topology-ip-flag enable
(config)# default sys clipId-topology-ip
The Status of LAG links in maps will start working after the next polling following an upgrade to ExtremeCloud IQ Site Engine. You can initiate the polling of a device by performing a refresh/rediscovery of the device.
ERS Device Configuration
ERS devices might automatically change VLAN configurations you define in ExtremeCloud IQ Site Engine. To disable this, change the vlan configcontrol setting for ERS devices you add to ExtremeCloud IQ Site Engine by entering the following in the device command line:
CLI commands
enable
config term
vlan configcontrol flexible
Additionally, configure all VLANs on the port for an ERS device with the same tag status (tagged or untagged). If enforcing to an ERS device on which a port has at least one VLAN as tagged, ExtremeCloud IQ Site Engine adds all untagged VLANs to the tagged VLAN list and clears the untagged VLAN list.
Creating an archive for ERS devices using the Network > Archives tab does not complete successfully if Menu mode (cmd-interface menu) is used instead of CLI mode (cmd-interface cli). See
SLX Device Configuration
When creating a ZTP+ Configuration for an SLX 9240 on which firmware version 18s.01.01 or 18s.01.02 is installed, the ZTP+ process fails if the Administration Profile value uses SSH or Telnet CLI credentials. ExtremeCloud IQ Site Engine indicates that the SSH or CLI profile is not supported by the device.
To create a ZTP+ configuration for an SLX 9240:
- Create a new Device Profile with the CLI Credential set to < No Access >.
- Create the ZTP+ Configuration and select the new Device Profile you created in Step 1 as the Administration Profile.
- After the ZTP+ process successfully completes and the device is added to ExtremeCloud IQ Site Engine, select a Device Profile that uses the correct CLI credentials for the SLX device in the Administration Profile.
| NOTE: | The SLX ZTP+ Connector does NOT support configuring CLI credentials on the device. |
ExtremeXOS Device Configuration
ExtremeXOS/Switch Engine devices on which firmware version 30.3.1.6 is installed do not download and install new firmware versions successfully via the ZTP+ process. To correct the issue, access the Network > Firmware tab in ExtremeCloud IQ Site Engine, select the ExtremeXOS device you are updating via ZTP+, and change the Version field in the Details right-panel from builds/xos_30.3/30.3.1.6 to 30.3.1.6.
Firmware Upgrade Configuration Information
ExtremeCloud IQ Site Engine supports firmware downloads and uploads to devices using TFTP, FTP, SCP, and SFTP. However, before firmware images can be downloaded or uploaded from the server, ExtremeCloud IQ Site Engine needs the root path or directory for each of the protocols. The following default root paths for each protocol are configurable from the Administration > Options > Inventory Manager tab:
Protocol Root Path:
- TFTP: /tftpboot/firmware/images/
- FTP: /tftpboot/firmware/images/
- SCP: /root/firmware/images/
- SFTP: /root/firmware/images/
To upload firmware images that are 2 GB or less to the server, use the ExtremeCloud IQ Site EngineNetwork > Firmware tab. For files larger than 2 GB, use a third-party client (such as SCP, WinSCP, or FTP).
For example, to use SCP to upload a firmware image to the SCP root path on the server, enter the following:
scp <LOCAL_FIRMWARE_PATH> root@<ExtremeCloud IQ Site Engine_SERVER_IP>:/root/firmware/images- Where:
- <ExtremeCloud IQ Site Engine_SERVER_IP>= IP Address to ExtremeCloud IQ Site Engine Server
- <LOCAL_FIRMWARE_PATH>= fully qualified path to a firmware image on the client machine
Wireless Manager Upgrade Information
A High Availability pair cannot be added as a flow source if the WLAN(s) selected are not in common with both wireless controllers.
Server and Client System Requirements
| IMPORTANT: | Wireless event collection is disabled by default in version 24.02.12 due to the increase in disk space usage required. To enable event collection, select Enable Event CollectionEvent Analyze. Then selectAdministration > Options > Event Analyze. Internet Explorer is not supported in ExtremeCloud IQ Site Engine version 24.02.12. |
ExtremeCloud IQ Site Engine Server Requirements
| Manufacturer | Operating System |
|---|---|
| Linux | Red Hat Enterprise Linux WS and ES v6 and v7 Ubuntu 20.04 |
| VMware® (ExtremeCloud IQ Site Engine Virtual Engine) | VMware ESXi™ 6.0 server VMware ESXi™ 6.5 server VMware ESXi™ 6.7 server VMware ESXi™ 7.0 server vSphere (client only)™ |
| Microsoft® Hyper-V (ExtremeCloud IQ Site Engine Virtual Engine) | Windows® Server 2012 R2 Windows® Server 2016 |
These are the operating system requirements for the ExtremeCloud IQ Site Engine server.
ExtremeCloud IQ Site Engine Client Requirements
These are the operating system requirements for remote ExtremeCloud IQ Site Engine client machines.
| Manufacturer | Operating System |
|---|---|
| Windows (qualified on the English version of the operating systems) | Windows® 10 and 11 |
| Linux | Red Hat Enterprise Linux WS and ES v6 and v7 Ubuntu 20.04 |
| Mac OS X® | Monterey |
ExtremeCloud IQ Site Engine Server and Client Hardware Requirements
These are the hardware requirements for the ExtremeCloud IQ Site Engine server and ExtremeCloud IQ Site Engine client machines.
| NOTES: | ExtremeControl and ExtremeAnalytics are not supported on Small ExtremeCloud IQ Site Engine servers. |
ExtremeCloud IQ Site Engine Server Requirements
| Small | Medium | Enterprise | Large Enterprise | |
|---|---|---|---|---|
| Total CPUs | 1 | 2 | 2 | 2 |
| Total CPU Cores | 8 | 16 | 24 | 24 |
| Memory | 16 GB | 32 GB | 64 GB | 64 GB |
| Disk Size | 240 GB | 480 GB | 960 GB | 1.92 TB |
| IOPS | 200 | 200 | 10,000 | 10,000 |
|
Recommended scale based on server configuration: |
||||
| Maximum APs | 250 | 2,500 | 25,000 | 25,000 |
| Maximum Wireless MUs | 2,500 | 25,000 | 100,000 | 100,000 |
| Maximum Managed Devices | 100 | 1,000 | 10,000 air gap 8,000 connected |
10,000 air gap 8,000 connected |
| ExtremeControl End-Systems | N/A | 50,000 | 200,000 | 200,000 |
| Statistics Retention (Days) | 90 | 180 | 180 | 360 |
| ExtremeAnalytics | No | Yes | Yes | Yes |
| MU Events | No | Yes | Yes | Yes |
| IMPORTANT: | For optimal performance the CPU and Memory needs to reserved in the ESX Client and the virtual machine needs to be deployed using Thick Disk provisioning. |
ExtremeCloud IQ Site Engine Client Requirements
| Requirements | |
|---|---|
| CPU Speed | 3.0 GHz Dual Core Processor |
| Memory | 8 GB (4 GB for 32-bit OS) |
| Disk Size | 300 MB (User's home directory requires 50 MB for file storage) |
| Java Runtime Environment (JRE) (Oracle Java only) | Version 8 |
| Browser1 (Enable JavaScript and Cookies) | Microsoft Edge Mozilla Firefox Google Chrome |
1Browsers set to a zoom ratio of less than 100% might not display ExtremeCloud IQ Site Engine properly (for example, missing borders around windows). Setting your browser to a zoom ratio of 100% corrects this issue.
Virtual Engine Requirements
The ExtremeCloud IQ Site Engine, ExtremeControl, and ExtremeAnalytics virtual engines must be deployed on a VMWare or Hyper-V server with a disk format of VHDX.
- The VMWare ExtremeCloud IQ Site Engine virtual engines are packaged in the .OVA file format (defined by VMware).
- The Hyper-V ExtremeCloud IQ Site Engine virtual engines are packaged in the .ZIP file format.
| IMPORTANT: | For ESX and Hyper-V servers configured with AMD processors, the ExtremeExtremeAnalytics virtual engine requires AMD processors with at least Bulldozer based Opterons. |
ExtremeCloud IQ Site Engine Virtual Engine Requirements
| Specifications | Small | Medium | Enterprise |
|---|---|---|---|
| Total CPU Cores | 8 | 16 | 24 |
| Memory | 16 GB | 32 GB | 64 GB |
| Disk Size | 240 GB | 480 GB | 960 GB |
| IOPS | 200 | 200 | 10,000 |
|
Recommended scale based on server configuration: |
|||
| Maximum APs | 250 | 2,500 | 25,000 |
| Maximum Wireless MUs | 2,500 | 25,000 | 100,000 |
| Maximum Managed Devices | 100 | 1,000 | 10,000 air gap 8,000 connected |
| ExtremeControl End-Systems | N/A | 50,000 | 200,000 |
| Statistics Retention (Days) | 90 | 180 | 180 |
| ExtremeAnalytics | No | Yes | Yes |
| MU Events | No | Yes | Yes |
| IMPORTANT: | For optimal performance the CPU and Memory needs to reserved in the ESX Client and the virtual machine needs to be deployed using Thick Disk provisioning. |
ExtremeControl Virtual Engine Requirements
| Specifications | Small | Medium | Enterprise | Large Enterprise |
|---|---|---|---|---|
| Total CPU Cores | 8 | 16 | 16 | 20 |
| Memory | 12 GB | 16 GB | 32 GB | 48 GB |
| Disk Size | 40 GB | 120 GB | 120 GB | 120 GB |
| IOPS | 200 | 200 | 200 | 200 |
|
Recommended scale based on server configuration: |
||||
| ExtremeControl End-Systems | 3,000 | 6,000 | 9,000/12,0001 | 12,000/24,0002 |
| Authentication | Yes | Yes | Yes | Yes |
| Captive Portal | No | Yes | Yes/No1 | Yes/No2 |
| Assessment | No | Yes | No | No |
1 The Enterprise ExtremeControlengine configuration supports two different scale options:
|
||||
2 The Large Enterprise ExtremeControlengine configuration supports two different scale options:
|
||||
| IMPORTANT: | For optimal performance the CPU and Memory needs to reserved in the ESX Client and the virtual machine needs to be deployed using Thick Disk provisioning. |
ExtremeAnalytics Virtual Engine Requirements
| Specifications | Small | Medium | Enterprise |
|---|---|---|---|
| Total CPU Cores | 8 | 16 | 16 |
| Memory | 12 GB | 32 GB | 64 GB |
| Disk Size | 40 GB | 480 GB | 960 GB |
| IOPS | 200 | 10,000 | 10,000 |
|
Recommended scale based on server configuration: |
|||
| Flows Per Minute | 250,000 | 500,000 | 750,000 |
| End-Systems | 10,000 | 20,000 | 30,000 |
| Raw Flow Retention (Days) | 3.5 | 3.5 | 7 |
| IMPORTANT: |
The ESXi free license supports a maximum of 8 CPU cores, and the medium and enterprise ExtremeAnalytics virtual engine installations require 16 CPU cores. Sixteen CPU cores are only available by purchasing a permanent license. To use the ExtremeAnalytics virtual engine with an ESXi free license, adjust the number of CPU cores to 8. To reduce the possibility of impaired functionality, ensure at least 4 GB of swap space is available for flow storage on the ExtremeAnalytics virtual engine. To verify the amount of
available RAM on your Linux system, use the |
Fabric Manager Requirements
| Specifications | Requirements |
|---|---|
| Total CPU Cores | 4 |
| Memory | 9 GB |
| Memory allocated to Java: -Xms -Xmx |
4 GB 6 GB |
| Disk Size | 60 GB |
ExtremeControl Agent OS Requirements
The table below outlines the supported operating systems for end-systems connecting to the network through an ExtremeControl deployment that is implementing agent-based assessment. Additionally, the end-system must support the operating system disk space and memory requirements as provided by Microsoft® and Apple®.
| Manufacturer | Operating System | Operating System Disk Space | Available/Real Memory |
|---|---|---|---|
| Windows1 | Windows Vista Windows XP Windows 2008 Windows 2003 Windows 7 Windows 8 Windows 8.1 Windows 10 |
80 MB | 40 MB (80 MB with Service Agent) |
| Mac OS X | Catalina Tiger Snow Leopard Lion Mountain Lion Mavericks Yosemite El Capitan Sierra |
10 MB | 120 MB |
1Certain assessment tests require the Windows Action Center (previously known as Windows Security Center), which is supported on Windows XP SP2+, Windows Vista, and Windows 7, Windows 8, and Windows 8.1 operating systems.
ExtremeControl Agent support for Antivirus or Firewall products includes, but is not limited to, the following families of products:
- McAfee
- Norton
- Kaspersky
- Trend Micro
- Sophos
ExtremeControl Agent operating system support for the above products includes the latest Windows or Mac OS X versions currently available at the time of product release. The ExtremeControl Agent running on MAC Operating Systems requires Java Runtime Environment (JRE) support. Some features of various products might not be supported. For additional information on specific issues, see Known Restrictions and Limitations.
ExtremeControl Supported End-System Browsers
The following table outlines the supported desktop and mobile end-system browsers connecting to the network through the Mobile Captive Portal of Extreme NetworksExtremeControl.
| Medium | Browser |
|---|---|
| Desktop | Microsoft Edge Microsoft Internet Explorer Mozilla Firefox Google Chrome |
| Mobile | Internet Explorer Mobile Microsoft Edge Microsoft Windows 10 Touch Screen Native (Surface Tablet) iOS Native Android Chrome Android Native Dolphin Opera |
| NOTES: | A native browser indicates the default, system-installed browser. Although this might be Chrome (Android), this also includes the default, system-controlled browser used for a device’s Captive Network Detection for a device. Typically, this is a non-configurable option for Wi-Fi Captive Network Detection, but default Android, Microsoft and iOS devices are tested for compatibility with the Mobile Captive Portal. A mobile device can access the standard (non-mobile) version of the Captive Portal using any desktop-supported browsers available on a mobile device. |
For other browsers, the Mobile Captive Portal requires the browser on the mobile device to be compatible with Webkit or Sencha Touch.
To confirm compatibility with Webkit or Sencha Touch, open http://<ExtremeControlEngine IP>/mobile_screen_preview using your mobile web browser.
- If the browser is compatible, the page displays properly.
- If the browser is not compatible with the Mobile Captive Portal, the following error displays:
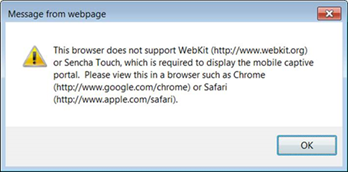
ExtremeControl Engine Version Requirements
For complete information on ExtremeControl engine version requirements, see Important Upgrade Information.
ExtremeControl VPN Integration Requirements
VPN concentrators are supported for use in ExtremeControl VPN deployment scenarios.
- Supported Functionality: Authentication and Authorization (policy enforcement)
Cisco ASA
Enterasys XSR - Supported Functionality: Authentication
Juniper SA (requires an S-Series Stand Alone (SSA) system in order to provide access control)
| NOTE: | For all ExtremeControl VPN Deployment scenarios, an S-Series Stand Alone (SSA) system is required to change authorization levels beyond the initial authorization, such as when using assessment. |
ExtremeControl SMS Gateway Requirements
The following SMS Gateways have been tested for interoperability with ExtremeControl:
- Clickatell
- Mobile Pronto
ExtremeControl SMS Text Messaging Requirements
The following mobile service providers are supported by default for SMS text messaging in an ExtremeControl deployment. Additional service providers can be added:
| AT&T | Sprint PCS |
| Alltel | SunCom |
| Bell Mobility (Canada) | T-Mobile |
| Cingular | US Cellular |
| Metro PCS | Verizon |
| Rogers (Canada) | Virgin Mobile (US and Canada) |
ExtremeAnalytics Requirements
To use an ExtremeSwitching X440-G2 switch as an Application Telemetry source for ExtremeAnalytics, install firmware version 22.4.1.4-patch2-5 or higher.
Ekahau Maps Requirements
ExtremeCloud IQ Site Engine supports importing Ekahau version 8.x maps in .ZIP format.
Guest and IoT Manager Requirements
Guest and IoT Manager Server OS Requirements
These are the operating system requirements for Guest and IoT Manager server:
| Manufacturer | Operating System |
|---|---|
| VMware® (ExtremeCloud IQ Site Engine Virtual Engine) | VMware ESXi™ 5.5 server VMware ESXi™ 6.0 server VMware ESXi™ 6.5 server vSphere (client only)™ |
Guest and IoT Manager Outlook Add-in Client Requirements
These are the requirements for the Client Machines, which need to run Guest and IoT Manager Outlook Add-in.
| Manufacturer | Operating System |
|---|---|
| Windows1 | Windows 7 Windows 10 |
| Mac OS X | Sierra High Sierra Mojave |
1Microsoft® Outlook® 2016 is needed on Windows/Mac clients for the add-in to operate.
Guest and IoT Manager Virtual Engine Requirements
The VMWare Guest and IoT Manager virtual engines are packaged in the .OVA file format (defined by VMware) and needs an x86, 64-bit capable environment
| Specifications | Minimum | Recommended |
|---|---|---|
| Total CPU Cores | 2 | 4 |
| Memory | 2 GB | 4 GB |
| Disk Size | 80 GB | 80 GB |
| Interfaces | 1 Physical NIC | 3 Physical NICs |
Guest and IoT Manager Supported Browsers
The following table outlines the supported desktop and mobile browsers that can be used to launch Guest and IoT Manager Admin and Provisioner Web Application:
| Medium | Browser | Version |
|---|---|---|
| Desktop | Microsoft Internet Explorer Mozilla Firefox Google Chrome Microsoft Edge Safari |
11 and later 63 and later 65 and later 42 and later 12 and later |
| Mobile1 | iOS Native Android Chrome US Browser Opera Firefox |
9 and later 65 and later 11.5 and later 40 and later 63 and later |
1Mobile Browsers are supported only for the Guest Self-Service Provisioning flow.
| NOTES: |
|
Getting Help
If you require assistance, contact Extreme Networks using one of the following methods:
- Extreme Portal
- Search the GTAC (Global Technical Assistance Center) knowledge base, manage support cases and service contracts, download software, and obtain product licensing, training, and certifications.
- The Hub
- Connect with other Extreme customers, ask or answer questions, and share ideas and feedback. This community is monitored by Extreme Networks employees, but is not intended to replace specific guidance from GTAC.
- GTAC
- For immediate support, call 1-800-998-2408 (toll-free in U.S. and Canada) or 1-603-952-5000.
Before contacting Extreme Networks for technical support, have the following information ready:
- Your Extreme Networks service contract number and/or serial numbers for all involved Extreme Networks products
- A description of the failure
- A description of any action already taken to resolve the problem
- A description of your network environment (such as layout, cable type, other relevant environmental information)
- Network load at the time of trouble (if known)
- The device history (for example, if you have returned the device before, or if this is a recurring problem)
- Any related Return Material Authorization (RMA) numbers