ExtremeAnalytics uses fingerprints to identify to which application a network traffic flow belongs. A fingerprint is a description of a pattern of network traffic which can be used to identify an application. ExtremeCloud IQ Site Engine provides thousands of system fingerprints with the ExtremeAnalytics feature. In addition, you can modify these fingerprints and create new custom fingerprints.
For additional information, see Getting Started with ExtremeAnalytics.
This Help topic provides the following information:
- Adding a Fingerprint
- Modifying a Fingerprint
- Enabling or Disabling a Fingerprint
- Deleting a Custom Fingerprint
- Updating Fingerprints
In order to add and modify fingerprints, you must be a member of an authorization group assigned the ExtremeCloud IQ Site Engine ExtremeAnalytics Read/Write Access capability.
Adding a Fingerprint
Use the following steps to add a new custom fingerprint based on an existing flow in the Applications Flows view.
- Select the Analytics tab and then select the Application Flows view.
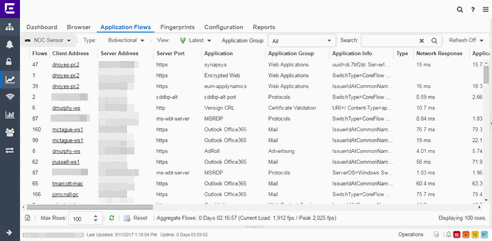
- Select the flow in the table that you want to base your new custom fingerprint on.
- Right-click on the flow and select the Fingerprints > Add Fingerprint option. The Add Fingerprint window opens.
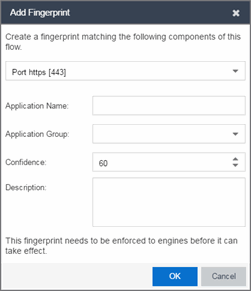
- Use the drop-down list to select the flow components on which to base the fingerprint. The options vary depending on the fingerprint you initially selected.
- Port <port number> — Creates a fingerprint that identifies traffic either coming from or going to the specified port.
- Address <IP address> on port <port number> — Creates a fingerprint that identifies traffic either coming from or going to this IP address on the specified port.
- Address <IP address> with mask on port <port number> — Creates a fingerprint that identifies traffic either coming from or going to the specified subnet on the specified port. For example, an IP address of 192.168.0.0 with a mask of 16 would result in all traffic either coming from or going to the 192.168 subnet on the specified port to be identified by the fingerprint.
- Host <host name> — Creates a fingerprint that identifies a specific hostname in the URI of web traffic.
- HTTP Header — Creates a fingerprint that identifies traffic containing specified HTTP header information, if HTTP header information is included in the flow's metadata.
Note that there can be two port number or IP address options listed: one for the flow's source port/IP address and one for the flow's destination port/IP address.
- If you selected an IP address with mask option, you need to specify a subnet of IP addresses. Enter the IP CIDR mask, which is a mask on the flow IP, with 0-32 for IPv4 and 0-128 for IPv6.
- Enter the name of the application for which the fingerprint is defined.
- Use the drop-down list to select the application group to which the application belongs. If none of the existing groups are appropriate, you can enter a new group name and the new group is automatically created.
- Select the fingerprint's confidence level. The confidence level defines the reliability of this fingerprint. Higher confidence fingerprints override lower confidence fingerprints, if multiple fingerprints match a flow. Values are 1-100, with 100 being absolutely reliable.
- Enter a description of the fingerprint, if desired.
- Select Save. The new fingerprint is created on the ExtremeCloud IQ Site Engine server.
- Enforce to push the new fingerprint to your engines.
| TIP: | You can also create a custom fingerprint from the Fingerprints tab. Select the Menu icon and select Create Fingerprint. The Add Fingerprint window opens where you can select all the flow components you want for the fingerprint. The new fingerprint is not based on an existing fingerprint and you need to enter values for all required fields such as IP or Hostname, Application Name, and Application Group. The new fingerprint must be enforced to engines before it can take effect. |
Modifying a Fingerprint
Modify a fingerprint's application name, application group, confidence level, and description from the Fingerprints tab.
- Select the Analytics > Fingerprints tab.
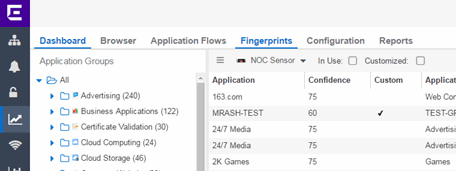
- Right-click on the desired fingerprint and select Modify Fingerprint from the menu. The Modify Fingerprint window opens.
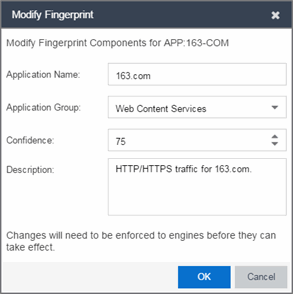
- Make the desired changes:
- Application Name — The name of the application that the fingerprint detects. If you change the application name, you are prompted to select whether to change the application name for only the currently selected fingerprint or for all fingerprints that have that same application name.
NOTE: If you change both the Application Name and Application Group:
If the new Application Name matches an existing name, the application group changes to the new group for all fingerprints with that new name, regardless of whether you choose to change the name for only the selected fingerprint or for all fingerprints with that name.
- Application Group — Organizes fingerprints into different types of applications such as Web applications or Business applications. You can sort the Application Flows view by application group, making it easier to view the data. If you change the application group for a fingerprint, it changes the group for all fingerprints with that same application name. If none of the existing groups are appropriate, you can create a new group by entering a new group name.
- Confidence — Defines the reliability of this fingerprint. Higher confidence fingerprints override lower confidence fingerprints, if multiple fingerprints match a flow. Values are 1-100, with 100 being absolutely reliable. The confidence level only applies to the currently selected fingerprint.
- Description — A description of the fingerprint. The description only applies to the currently selected fingerprint.
- Application Name — The name of the application that the fingerprint detects. If you change the application name, you are prompted to select whether to change the application name for only the currently selected fingerprint or for all fingerprints that have that same application name.
- Select OK.
- Enforce to push the change to your engines.
Enabling or Disabling a Fingerprint
Enable or disable a fingerprint from the Fingerprints tab. When a fingerprint is enabled, it is used to identify applications. When it is disabled, it is ignored.
- Select the Analytics > Fingerprints tab.
- Right-click on the desired fingerprint in the Fingerprints table and select either Enable Fingerprint or Disable Fingerprint.
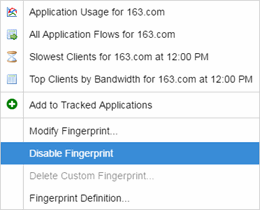
- Enforce to push the change to your engines.
| NOTE: | If you disable a system fingerprint, it becomes a custom fingerprint. If you then enable the fingerprint, it remains a custom fingerprint. Deleting the custom fingerprint reloads the original system fingerprint. |
Deleting a Custom Fingerprint
Delete a custom fingerprint from the Fingerprints tab. A custom fingerprint is either a new user-defined fingerprint, a modification of a system fingerprint, or a disabled fingerprint. (Custom fingerprints can be identified by a 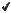 in the Custom column.)
in the Custom column.)
When you delete a custom fingerprint, it is removed entirely. If you delete a custom fingerprint overriding a system fingerprint, the original system fingerprint is reloaded. System fingerprints that have not been modified cannot be deleted, however, they can be disabled.
Use these steps to delete a custom fingerprint:
- Select the Analytics tab in ExtremeCloud IQ Site Engine and then select the Fingerprints view
- Right-click on the desired fingerprint in the Fingerprints table and select Delete Custom Fingerprint. The Delete Fingerprint window opens.
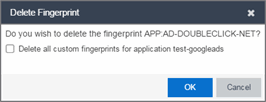
- You can delete only the selected fingerprint or select the option to delete all custom fingerprints that match the application name of the selected fingerprint.
- Select OK. If a custom fingerprint overrides a system fingerprint, then deleting the custom fingerprint reloads the original system fingerprint.
- Enforce to push the change to your engines.
Updating Fingerprints
New and updated fingerprints are provided via a fingerprint update website. Perform a one-time manual update of the fingerprint database or configure a scheduled update to be performed automatically from the Configuration tab. Custom fingerprints are not overwritten when an update is performed.
When a fingerprint update is performed, the fingerprint update server is checked for newer fingerprints than what is available on the ExtremeCloud IQ Site Engine server. If there are newer fingerprints, they are downloaded, and the fingerprint definitions are updated with any new fingerprint definition files. You need to enforce your engines following an update to push the updated fingerprints to the engines.
Perform a Fingerprint Update
Perform a manual one-time update of the fingerprint database. To access the update website, you need to create an Extranet account at ExtremeNetworks.com and define a username and password for the account. You need the username and password in order to perform updates.
- Select the Analytics tab in ExtremeCloud IQ Site Engine and then select the Configurations view.
- In the left-panel tree, expand the System folder and select Fingerprints.
- Select the Menu icon (
 ) and select Update Fingerprints. If you have already configured your Fingerprint Update settings, the update is performed immediately.
) and select Update Fingerprints. If you have already configured your Fingerprint Update settings, the update is performed immediately.
If you have not configured your settings, the Fingerprint Update window opens.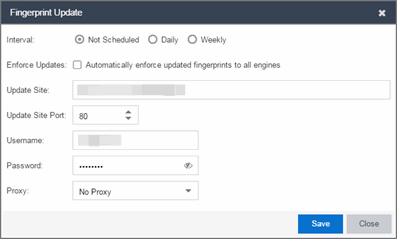
- Leave the Interval selection as Not Scheduled.
- Select the Enforce Updates checkbox to automatically update fingerprints on all engines. Not selecting this checkbox requires you to update each engine manually.
- The Update Site field displays the default path to the official fingerprint update site. Typically, this field does change unless for security reasons the system does not have access to the internet and an internal update site must be used.
- The Update Site Port is the port on the update site to which the update connects. The port cannot be changed unless you are using a custom update site.
- Enter the credentials used to access the fingerprint update website. These are the username and password credentials you defined when you created an Extranet account at ExtremeNetworks.com.
- If your network is protected by a firewall, you need to configure proxy server settings to use when accessing the website. In the Proxy field, select Use Proxy or Use Proxy with Credentials and enter your proxy server address and port ID. (Consult your network administrator for this information.) If your proxy server requires authentication, enter the proxy username and password credentials. The credentials you add here must match the credentials configured on the proxy server.
- Select Save. The Fingerprint Update is performed immediately.
- If you did not select the Enforce Updates checkbox, enforce to push the changes to your engines when the update is complete.
Schedule Fingerprint Updates
You can schedule fingerprint updates performed automatically on a daily or weekly basis.
To access the update website, you need to create an Extranet account at ExtremeNetworks.com and define a username and password for the account. You need the username and password in order to schedule updates.
- Select the Analytics tab in ExtremeCloud IQ Site Engine and then select the Configuration view.
- In the left-panel tree, expand the System folder and select Fingerprints.
- Select the Menu icon (
 ) and select Fingerprint Update Settings. The Fingerprint Update window opens.
) and select Fingerprint Update Settings. The Fingerprint Update window opens.
- Select the update interval which defines how frequently the update is performed: Daily or Weekly.
- If you have selected Weekly, select the day of the week you would like the update performed.
- Enter the scheduled time you would like the update performed.
- Select the Enforce Updates checkbox to automatically update fingerprints on all engines. Not selecting this checkbox requires you to update each engine manually.
- The Update Site field displays the default path to the official fingerprint update site. Typically, this field does not change unless for security reasons the system does not have access to the internet and an internal update site must be used.
- The Update Site Port is the port on the update site to which the update connects. The port cannot be changed unless you are using a custom update site.
- Enter the credentials used to access the fingerprint update website. These are the username and password credentials you defined when you created an Extranet account at ExtremeNetworks.com.
- If your network is protected by a firewall, configure proxy server settings to use when accessing the website. In the Proxy field, select Use Proxy or Use Proxy with Credentials and enter your proxy server address and port ID. (Consult your network administrator for this information.) If your proxy server requires authentication, enter the proxy username and password credentials. The credentials you add here must match the credentials configured on the proxy server.
- Select Save.
- If you did not select the Enforce Updates checkbox, enforce to push the changes to your engines when the update is complete.
For information on related help topics: