This Configuration Evaluation Wizard is used to test the rules defined in your Access Control Configuration in order to determine what behavior an end-system encounters when it is authenticated on an Access Control engine. To access this window, select Configurations in the left-panel of the Access Control tab, select an Access Control Configuration in the main panel, and select the Evaluate button in the toolbar.
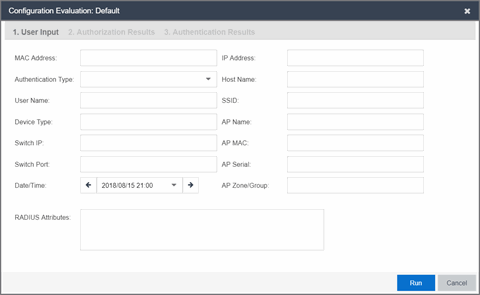
User Input
Enter the end-system data on which you are evaluating the Access Control configuration in this tab.
Authentication Results Tab
This tab displays the set of RADIUS servers and LDAP servers by which ExtremeControl processes an end-system request.
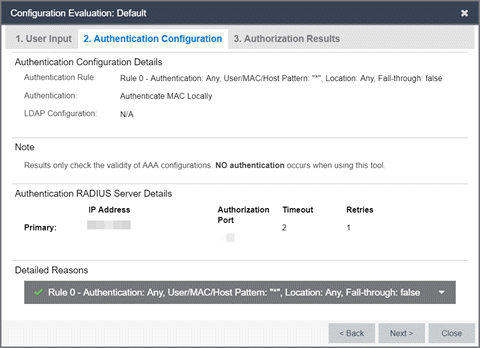
- Authentication Result Details
-
- Authentication Rule - A description of the authentication type and user name expression used for the AAA entry that the ExtremeControlengine uses to authenticate the end-system. For a Basic AAA Configuration, this is always: Authentication: Any, User Pattern"*". Additionally, indicates whether fall-through functionality is enabled for the Configuration.
- Authentication - For MAC authentication requests, this field displays whether the request is authenticated locally or proxied to the RADIUS server.
- LDAP Configuration - The LDAP configuration used to obtain any LDAP data for the end-system, if applicable.
- Authentication RADIUS Server Details
- This section lists the IP address, port, shared secret, timeout, and retries listed for all the RADIUS servers used to authenticate the end-system request, if it needs to be proxied.
- Detailed Reasons
- This section is only applicable for an Advanced AAA Configuration. It lists why a request passed or failed the definition of each AAA entry as well as whether fall-through functionality is enabled.
Authorization Results Tab
This tab displays information detailing the method by which the end-system is authorized, according to the parameters and rules of the selected Access Control Configuration. The results also factor in any RADIUS user attributes you enter on the User Input tab when the evaluation is run.
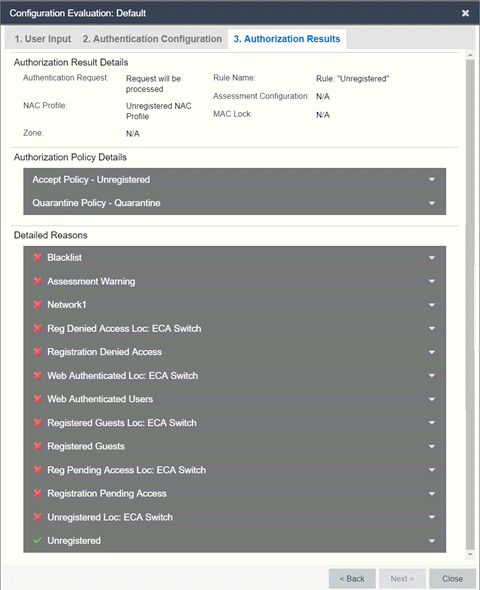
- Authorization Result Details
-
- Authentication Request - Displays whether the ExtremeControl engine processes the request, or reject the request based on a MAC Lock or a rule that assigns an Access Control Profile configured to reject the user.
- Rule Name - The name of the rule that the end-system passed.
- NAC Profile - The Access Control Profile assigned to the end-system by the rule.
- Assessment Configuration - The assessment configuration used by the Access Control Profile, if any.
- MAC Lock - The MAC Lock assigned to the end-system, if any.
- Authorization Policy Details
- This section displays the RADIUS response attributes returned for end-systems in specific states. Possible states are Accept, Quarantine, Assessing, and Failsafe. Expand each state to view the RADIUS attributes. These are the RADIUS attributes returned for the switch IP that is listed in the End-System Details section.
- Detailed Reasons
- This section lists all the rules from the Access Control Configuration that were evaluated during the end-system authentication. Rules are only evaluated until one of them is passed. Each rule listing can be expanded to view why the end-system passed or failed that rule.
For information on related help topics: