This tab provides information about an ExtremeControl engine's configuration. The information changes depending on the type of engine selected in the left-panel tree.
To access this tab, select an ExtremeControl engine in the left-panel tree, then select the Details tab in the right panel.
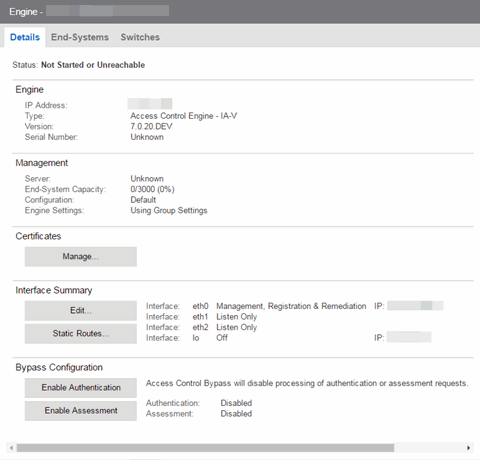
- General Information
- This section displays general information about the ExtremeControl engine, including its name, IP address, type (ExtremeControl Gateway or Layer 2/Layer 3 ExtremeControl Controller), the engine version, the IP address of the ExtremeCloud IQ Site Engine Management server, and the ExtremeControlengine status.
- End-System Capacity
- This field lists the engine's current capacity, which is the number of end-systems that authenticated within the last 24 hours out of the maximum number of authenticating end-systems supported for the engine.
- ExtremeControl Configuration
- Displays the ExtremeControl Configuration assigned to the engine. The ExtremeControl Configuration determines the ExtremeControl Profile assigned to an end-system connecting to the network.
- Engine Settings
- The engine settings configuration being used by your ExtremeControl engine. Engine settings are configurable in the Engine Settings window by selecting the Engine Settings button.
- Certificates
- Select Manage to update the ExtremeControl certificates in the Manage Certificates window.
- Interface Summary
- Displays a summary of the current engine interface configuration.
Select Edit to open the Interfaces window, where you can change the engine Host Name and Gateway..
Select Static Routes to open the Static Routes window, where you can add or edit the static routes used for advanced routing configuration..
- ExtremeControl Bypass Configuration
- The ExtremeControl Bypass Configuration feature allows you to bypass ExtremeControl processing of authentication requests from end-systems connecting to the
network and also disable the ExtremeControl assessment process. For ExtremeControlauthentication bypass, ExtremeControl either configures the switch to authenticate directly to a RADIUS server to which ExtremeControl is configured to proxy authentication requests, or it disables RADIUS authentication on the switch. This capability is useful for troubleshooting purposes. For example, if there is a problem with an ExtremeControl Configuration, the Disable button lets you remotely disable ExtremeControl functionality until the problem is resolved. You can then use the Enable button to re-enable ExtremeControl functionality on the engines. When ExtremeControl authentication or assessment is disabled, the ExtremeControl engine name and IP address display in red text in the left-panel tree indicating the engine is in Bypass mode.
For ExtremeControl Gateway engines, when you select the option to disable ExtremeControl authentication processing, if proxy RADIUS servers are configured for authentication in a Basic AAA Configuration, the ExtremeControl Engine configures the switches to send RADIUS packets directly to the primary and secondary RADIUS servers (from the Basic AAA Configuration), instead of talking to the RADIUS proxy through the ExtremeControl gateway. RADIUS authentication is not disabled on the switch, and end users still need to authenticate in order to connect to the network. The switches must be defined in the back-end proxy RADIUS server as RADIUS clients with the same shared secret used by the ExtremeControl Gateway engines. If there are no proxy RADIUS servers configured in a Basic AAA Configuration, or if an Advanced AAA Configuration is used, RADIUS authentication on the switch is disabled when ExtremeControl authentication processing is disabled.
NOTES: If you have disabled ExtremeControl authentication processing and then enforce with new switches, the new switches are configured to send RADIUS packets directly to the primary and secondary RADIUS servers. These switches are reconfigured to talk to the RADIUS proxy when you enable ExtremeControl; a second enforce is not necessary.
Bypass is not an option for switches set to Manual RADIUS Configuration or ExtremeWireless controllers not configured for RADIUS strict mode.For ExtremeControl Controller engines, when you disable ExtremeControl authentication, then the ExtremeControl Controller does not send RADIUS packets directly to the RADIUS servers. Authentication is disabled on the ExtremeControl Controller and end-systems do not need to authenticate to the network. Traffic from the end-systems bypass the ExtremeControl Controller and go directly onto the network.
The Status fields provide the current status of the ExtremeControl authentication or assessment process. The authentication status field also includes a link to the Verify RADIUS Configuration on Switches feature. This feature is available for ExtremeControl Gateway engines and Layer 2 ExtremeControl Controllers, and can be used to alert you to any RADIUS configurations that are out of sync and could cause RADIUS authentication problems on the network.