Use the Add LDAP Configuration window to configure the LDAP servers on
your network. You can access this window from the Control > Access Control tab. Expand the Configuration > Configurations > AAA > LDAP Configurations folder in the right panel and select Add.
You can also access this window from the Manage LDAP Configurations
tab.
Any changes made in this window are written immediately to the ExtremeCloud IQ Site Engine
database.
| NOTE: | If you are using LDAPS, your ExtremeCloud IQ Site Engine/ExtremeControl environment must be configured to
accept the new LDAPS server certificate. For information, see Server Certificate Trust Mode in the Secure Communications Help topic. |
|---|
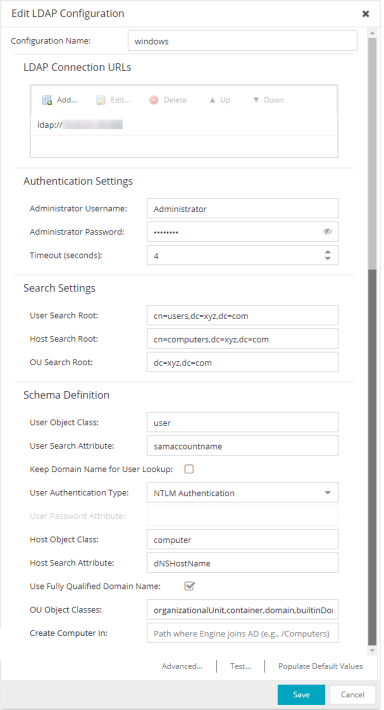
- LDAP Connection URLs
- Use this table to add, edit, or delete connection URLs for the LDAP
server and any backup servers you have configured. (The backup servers
are redundant servers containing the same directory information.)
Use the Up and Down arrows to arrange the order that the URLs are listed.
The format for the connection URL isldap://host:portwhere host equals hostname or IP address, and the default port is 389. For example,ldap://10.20.30.40:389. If you are using a secure connection, the format isldaps://host:portand the default port is 636. For example,ldaps://10.20.30.40:636. If you are using LDAPS, yourExtremeCloud IQ Site Engine/ExtremeControl environment must be configured to accept the new LDAPS server certificate. For information, see Server Certificate Trust Mode in the Secure Communications Help topic.
If you are creating an LDAP configuration for Novell eDirectory, be aware that the eDirectory may require that the universal password lookup be done using LDAPS. If you configure the URL for LDAP only, the lookup may fail.
- Authentication Settings
- Enter the administrator username and password that will be used to connect to the LDAP server to make queries. The credentials only need to provide read access to the LDAP server. The timeout field lets you specify a timeout value in seconds for the LDAP server connection.
- Search Settings
- For the three fields, enter the root node of the LDAP server. To improve search performance, you can specify a sub tree node to confine the search to a specific section of the directory. The search root format should be a DN (Distinguished Name). If Nested Group Search is enabled, then groups are processed recursively which can impact the authorization delay.
- Schema Definition
- Provide information that describes how entries are organized in the LDAP server.
-
Schema Definition fields: -
- User Object Class- enter the name of the class used for users.
- User Search Attribute- enter the name of the attribute in the user object class that contains the user's login ID.
- Keep Domain Name for User Lookup- If selected, this option will allow the full username to be used when looking up the user in LDAP. For example, you should select this option when using the User Search Attribute: userPrincipalName.
If the option is not selected, the domain name will be stripped off the username prior to performing the lookup. For example, you should deselect this option when using the User Search Attribute: sAMAccountName. Two examples of the domain name being stripped off would be:
user@domain.com -> user
DOMAIN\user -> user - User Authentication Type- Specify how the user is authenticated. There are 4 options:
LDAP Bind– This is the easiest option to configure, but only works with a plain text password. It is useful for authentication from the captive portal but does not work with most 802.1x authentication types.
NTLM Authentication– This option is only useful when the backend LDAP server is really a Microsoft Active Directory server. This is an extension to LDAP bind that uses ntlm_auth to verify the NT hash challenge responses from a client in MsCHAP, MsCHAPV2, and PEAP requests. If you want to run a NTLM Health Check, see NTLM Health Check and Advanced for the additional configuration steps.
NT Hash Password Lookup– If the LDAP server has the user’s password stored as an NT hash that is readable by another system, you can have ExtremeControl read the hash from the LDAP server to verify the hashes within an MsCHAP, MsCHAPV2, and PEAP request.
Plain Text Password Lookup– If the LDAP server has the user’s password stored unencrypted and that attribute is accessible to be read via an LDAP request, then this option reads the user’s password from the server at the time of authentication. This option can be used with any authentication type that requires a password.
- User Password Attribute- This is the name of the password used with the NT Hash Password Lookup and Plain Text Password Lookup listed above.
- Host Object Class- enter the name of the class used for hostname.
- Host Search Attribute- enter the name of the attribute in the host object class that contains the hostname.
- Use Fully Qualified Domain Namecheckbox - use this checkbox to specify if you want to use the Fully Qualified Domain Name (FQDN) or just hostname without domain.
- OU Object Classes- the names of the classes used for organizational units.
- Create Computer In - the path in the Active Directory where Access Control Engines will be created (OU where Access Control Engines join the domain). The default value is empty. It translates to /Computers in the common AD.
- Advanced
- Advanced LDAP Configurationis only accessible when User Authentication Type is set to NTLM Authentication.The LDAP configuration information you enter here specifies a user account and domain to the user for the NTLM Health Check. To configure the Health Check tests:
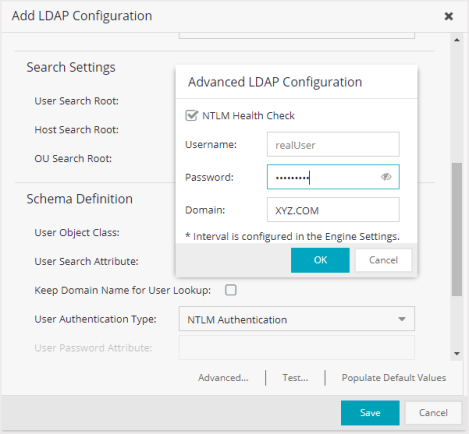
- Configure the interval and timeout for the test. See NTLM Health Check.
- Select NTLM Health Check.
- Enter the Username, Password, and theDomain to use for the health check tests.
- Select OK.
The Access Control Engine expects a positive response from the domain controller for the health check authentication. If timeout happens or a negative response is received, the failover occurs and the Access Control Lost Partial Contact with LDAP Service alarm is generated.
WARNING: - You should only use the health check in an environment where you have multiple domain controllers deployed.
- The health check should only be enabled if you have experienced this issue.
- The Domain password policy requirement for periodic password check should be disabled for the health check account. The credentials used by the health check should always be working.
- Test Button
- The connection to the LDAP server is tested and a report on connection test results is provided. There is also a user/host search that lets you search on a user entry or host entry value and display the attributes associated with those values.
- Populate Default Values Button
- Select from the defaults available from the menu:
- Active Directory: User Defaults- Settings that allow user authentication when ExtremeControl is set to proxy to LDAP and the server is an Active Directory machine.
- Active Directory: Machine Defaults- Settings that allow machine authentication when ExtremeControl is set to proxy to LDAP and the server is an Active Directory machine.
- Open LDAP Defaults -Settings that allow ExtremeControl to verify the user's password via an OpenLDAP server. See the NAC Manager How to Configure PEAP Authentication via OpenLDAP Help topic for information.
- Novell eDirectory Defaults- Settings that allow ExtremeControl to read the universal password from Novell eDirectory. You must configure eDirectory to allow that password to be read. See the NAC Manager How to Configure PEAP Authentication via eDirectory help topic for information.
For information on related help topics: