Use this window to add a new policy mapping or edit an existing policy mapping. A policy mapping specifies a policy role (created on the Policy tab) and/or any additional RADIUS attributes included as part of a RADIUS response to a switch (as defined in the Gateway RADIUS Attributes to Send field configured in the Edit Switch window). For additional information about configuring policy mappings, see How to Set Up Access Policies and Policy Mappings.
Access this window by selecting the Add or Edit toolbar buttons in the Edit Policy Mapping Configuration window.
The fields in this window vary depending on whether you are using a basic or advanced policy mapping configuration. For a definition of each field, see below.
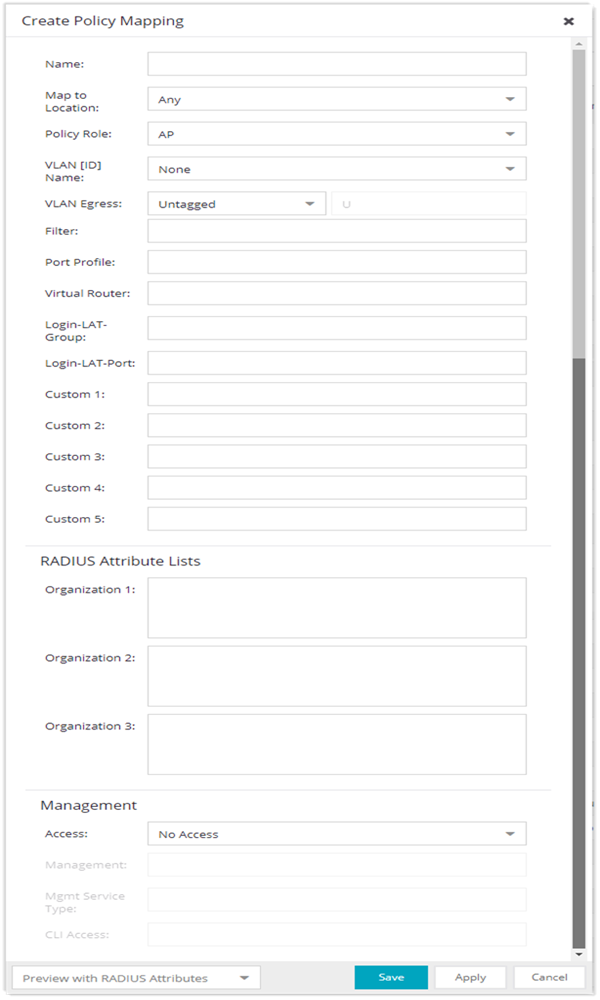
- Map to Location
- Allows you to specify a certain location for the mapping. You should first configure your locations using the Location Group (Control tab > ExtremeControl > ExtremeControl Configurations > Group Editor > Location Groups) or you can select the Edit button to the right of the field to add a location group to the list. For more information on using the Location option in Policy Mappings, see the Edit Policy Mapping Configuration Window Help topic.
- Policy Role
- Use the drop-down list to select a policy role, or enter a policy role in the
field. The drop-down list displays
any policy roles you have created and saved in the Policy tab
and/or all the policy roles contained in the ExtremeControl Controller policy
configuration.
Roles from all your policy domains are listed; if there are duplicate
names, only one is listed. The list is not case sensitive, so "Enterprise
User" and "enterprise user" are considered duplicate policy names. All
policy roles used in your mappings must be part of your ExtremeControl) Controller policy configuration and/or defined in Policy tab and enforced to the
EOS policy-enabled switches in your network.
NOTE: Entering a new policy role does not create a new role in the Policy tab.
- VLAN [ID] Name
- Use the drop-down list to select the appropriate VLAN associated with the policy. This list displays any VLANs defined in ExtremeCloud IQ Site Engine. Select the configuration menu button to the right of the field to add a VLAN to the list. VLANs you add remain in the list only as long as they are used in a mapping and they are not added to the ExtremeCloud IQ Site Engine database.
- VLAN Egress
- Use the drop-down list to select the appropriate VLAN the egress forwarding state: Tagged (frames are forwarded as tagged), Untagged (frames are forwarded as untagged), Same as Ingress (frames are forwarded as specified by the VLAN Ingress), or User Defined (you define how frames are forwarded).
- Filter
- If your network devices require a custom Filter-Id, enter it here. The Filter column typically maps to the Filter-Id RADIUS attribute. This value applies to ExtremeWireless Controllers and other switches that support the Filter-Id attribute.
- Port Profile
- For ExtremeXOS/Switch Engine devices on which legacy firmware is installed, this field indicates the profile used by Extreme Policy.
- Login-LAT-Port
- If you have ExtremeWireless Controllers on your network, the Login-LAT-Port is an attribute returned in the default RADIUS response. The Login-LAT-Port value is used by the controller to determine whether the authentication is fully authorized. A value of "1" indicates the authentication is authorized, where a value of "0" indicates that authorization is not complete. The value of "0" is used by the controller to determine that additional authentication is required and is a signal for the controller to engage its external captive portal and use HTTP redirection to force HTTP traffic from the end-system to the defined ExtremeControl engine. This is used in conjunction with the Registration and Assessment features of ExtremeControl.
- Custom
- If your network devices require additional RADIUS response attributes in order to provide authorization or define additional parameters for the authenticated session, you can define them in the five available Custom option fields.
- Organization 1-3
- Enter additional RADIUS response attributes in a single mapping in the Organization fields. For example, you can use each field to provide a complete ACL for a different third-party vendor.
- Management
- Enter a management attribute used to authenticate requests for administrative access to the selected switches, for example, "mgmt=su:", "mgmt=rw:", or "mgmt=ro:". The management attribute determines the level of access the administrator will have to the switch: superuser, read/write, or read-only. Be sure to include the final colon (":") in the attribute, or the management access will not work.
For information on related help topics: