In your ExtremeControl profiles, each access policy (Accept, Quarantine, Failsafe, and Assessment) is associated to a policy mapping that defines exactly how end-system traffic is handled on the network. Each mapping specifies a policy role (created in the Policy tab) and/or any additional RADIUS attributes included as part of a RADIUS response to a switch.
The RADIUS attributes required by a switch are specified in the Gateway RADIUS Attributes to Send field configured in the Edit Switch window. The actual switch RADIUS attribute values (Login-LAT-Port, Custom 1, etc.) are defined within each policy mapping configured in this window. Each policy mapping is associated with the access policy selected in your ExtremeControl profiles.
When an end-system authenticates to the network, the ExtremeControl profile is applied and the appropriate RADIUS response attributes are extracted from the mapping based on the switch the authentication request originated from. The attributes are returned to the switch in the RADIUS Access-Accept response.
For more information on configuring policy mappings, see How to Set Up Access Policies and Policy Mappings. For a description of each ExtremeControl access policy, and some guidelines for creating corresponding policy roles in the Policy tab, see the section on Access Policies in the Concepts file.
To access this window, select the Policy Mappings left-panel option in the ExtremeControl Configurations > Access Control left-panel menu.
The columns displayed in this window vary depending on whether you are using a Basic or Advanced policy mapping configuration. For a definition of each column, see below.
Basic AAA Configurations define the RADIUS and LDAP configurations for all end-systems connecting to your ExtremeControl engines.
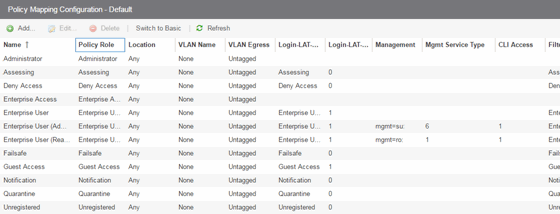
Advanced Policy Mapping Configuration
Column Definitions
- Name
- The policy mapping name.
- Policy Role
- The policy role assigned to this mapping. All policy roles used in your mappings must be part of your ExtremeControl (ExtremeControl) Controller policy configuration and/or defined in the Policy tab and enforced to the policy-enabled switches in your network.
- Location
- Policy mapping locations permit authentication requests that match the same ExtremeControl rule and corresponding ExtremeControl profile to be authorized to different accept attributes (policy/VLAN/Custom Attribute) based on the location the request originated from. For example, in the Policy Mapping Configuration screenshot above, the Administration policy mapping has five entries, with each entry assigning a different VLAN (for RFC 3580-enabled switches) for authentication requests matching the specified location. Requests originating from the 1st floor South location will be authorized to VLAN 100, and requests originating from the 2nd floor North location (matching the same ExtremeControl rule) is authorized to VLAN 220. Using locations in this manner lets you authorize end-systems to different access criteria using a single ExtremeControl rule, whereas the alternative would be to create multiple location-based ExtremeControl rules each with an ExtremeControl Profile that corresponds with the desired access value.
When policy mapping locations are used in this manner, it is important to include a catch-all policy mapping (the fifth Administration mapping in the example above) that has a location of "any" and sets the access behavior for an authorization originating from any other location. The access behavior could be a policy/VLAN/Custom Attribute that grants some form of restricted access, or denies access altogether. If a catch-all mapping is not included, a warning message appears on enforce indicating that there is no catch-all mapping configured, and authorizations that match the policy but do not originate from a defined location, can result in errors or unpredictable behavior.
- VLAN Name
- If you have RFC 3580-enabled switches in your network, this column displays the VLAN name assigned to this mapping.
- VLAN Egress
- If you have RFC 3580-enabled switches in your network, this column displays the VLAN ID assigned to this mapping.
- Filter
- This value is only displayed in Basic mode if ExtremeWireless Controllers have been added to ExtremeCloud IQ Site Engine. The Filter column typically maps to the Filter-Id RADIUS attribute. This value applies to ExtremeWireless Controllers and other switches that support the Filter-Id attribute.
- Login-LAT-Port
- If you have ExtremeWireless Controllers on your network, the Login-LAT-Port is an attribute returned in the default RADIUS response. The Login-LAT-Port value is used by the controller to determine whether the authentication is fully authorized. A value of "1" indicates the authentication is authorized, where a value of "0" indicates that authorization is not complete. The value of "0" is used by the controller to determine that additional authentication is required and is a signal for the controller to engage its external captive portal and use HTTP redirection to force HTTP traffic from the end-system to the defined ExtremeControl engine. This is used in conjunction with the Registration and Assessment features of ExtremeControl.
- Management
- The authorization attribute returned for successful administrative access authentication requests that originate from network equipment configured to use RADIUS as the authentication mechanism for remote management of switches, routers, VPN concentrators, etc. Examples of management values for EOS devices are: "mgmt=su:", "mgmt=rw:", or "mgmt=ro:". The management attribute determines the level of access the administrator will have when authorized to access the device: superuser, read/write, or read-only.
- Custom
- Some network devices require additional RADIUS response attributes in order to provide authorization or define additional parameters for the authenticated session. These additional attributes can be defined in the five available Custom option fields.
- Attribute List 1-3
- The Attribute List fields display additional RADIUS response attributes in a single mapping. For example, you can use each field to provide a complete ACL for a different third-party vendor.
For information on related help topics: