The rule General tab displays general information about the rule selected for a Service in the left-panel Roles/Services > Service Repository > Local or Global Services tab and enables you to change it. In addition, you can view and change the Traffic Description and Actions associated with the rule. Traffic Description identifies the type of traffic to which the rule pertains. Actions apply class of service, access control, and/or accounting and security behavior to packets matching the rule.
Any additions or changes you make to this tab must be enforced in order to take effect. If you modify an enabled rule's actions, the Policy tab checks for conflicts with other rules in the services and roles with which the newly modified rule is associated. See Conflict Checking for more information.
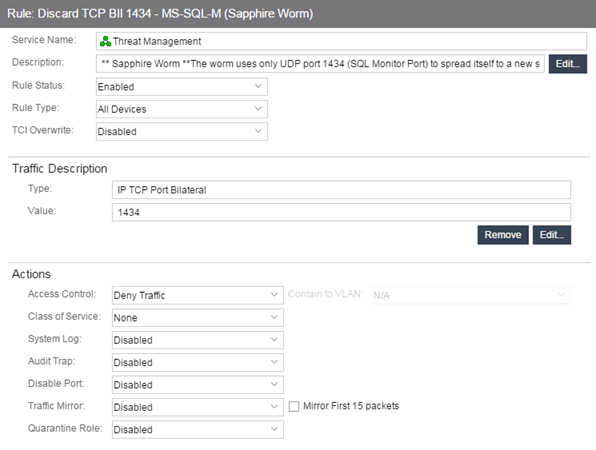
General Area
- Description
- Use the Edit button to open a window where you can enter or modify a description of the rule.
- Rule Status
- Lets you disable the rule, or enable it if it's already disabled. If the rule is disabled, it is unavailable for use by the current service, but can still be copied to other services and enabled, or re-enabled at another time for the current service. Disabling a rule is an alternative to deleting and recreating it. The rule icon in the left panel displays a red X if the rule is disabled.
- Rule Type
- Use the drop-down list to select the types of devices to which you wish this rule to apply
when enforced. The recommended selection is All Devices, unless there is a
specific need for a device-specific rule. If this need arises, the Rule Type
feature enables services to be customized to contain rules specific to a
device's type when support for a traffic description and/or action is not
be available on all managed devices.
For device-specific rules, only those traffic descriptions supported on the device are available when you define the rule's traffic description on this tab. For All Devices rules, all traffic descriptions are available; however, you must be aware that you cannot enforce the rule to a device on which it is not supported.
- TCI Overwrite
- Specify the TCI Overwrite functionality for the rule:
- Enabled — Enabling TCI Overwrite enables the VLAN (access control) and class of service characteristics defined in this rule to overwrite the VLAN or class of service (CoS) tag in a received packet, if that packet has already been tagged with VLAN or CoS information.
- Disabled — If this option is disabled the TCI Overwrite option is ignored, but lower-precedence rules and the role default actions can still specify TCI Overwrite for the data packet if there is a match.
- Prohibited — Do not set TCI Overwrite for this data packet, even when a lower-precedence rule or the role default actions has the TCI Overwrite option set to enabled.
Traffic Description Area
The Traffic Description area enables you to view and change the traffic description associated with a rule. The Traffic Description identifies the traffic classification type for the rule. Rules enable you to assign access control (VLAN membership) and/or class of service to network traffic depending on the traffic's classification type.
- Value
- Displays the values/parameters selected for the rule's Classification Type. See Classification Types and their Parameters for parameter information.
- Edit Button
- If a Traffic Description Type has been defined for the rule, selecting Edit opens the Edit Rule window, where you can edit the parameters or values for the rule's classification type.
Actions Area
The Actions area enables you to view and change the actions associated with a rule. Actions apply access control, class of service, security, and/or accounting behavior to packets matching the rule.
- Access Control
- Use this drop-down list to select the appropriate access control for the rule. You can
permit traffic
to be forwarded, deny traffic altogether, or contain traffic to a VLAN.
Select None to disable access control for this rule.
- Permit Traffic — enables traffic to be forwarded with the port's assigned VID.
- Deny Traffic — traffic will be automatically discarded.
- Contain to VLAN — contains traffic to a specific VLAN. Use the drop-down list to select the desired VLAN.
- Class of Service
- Use the drop-down list to select a class of service to associate with the rule. The Policy tab lets you define classes of service that each include an 802.1p priority, and optionally an IP type of service (ToS/DSCP) value, rate limits, and transmit queue configuration. You can then assign a class of service as a classification rule action. See Getting Started with Class of Service and How to Create a Class of Service for more information. Select None to disable class of service for this rule.
When rule accounting is enabled on a device, each rule keeps a list of the ports on which it has been used. Use the following three options to specify certain rule usage actions to take place when a "rule hit" is reported.
- System Log
- Specify System Log functionality for the rule.
- Enabled — If this option is enabled, a syslog message is generated when the rule is used. This option must be enabled if you are configuring Policy Rule Hit Reporting on your devices.
- Disabled — If this option is disabled and this rule is hit, it does not generate a Syslog message, but lower-precedence rules and the role default actions can still specify a syslog message be sent for this data packet if there is a match.
- Prohibited — If this rule is hit, no syslog message is generated for this data packet, even when a lower-precedence rule or the role default actions has the System Log action set to enabled.
- Audit Trap
- Specify Audit Trap functionality for the rule:
- Enabled — If this option is enabled, an audit trap is generated when the rule is used.
- Disabled — If this option is disabled and this rule is hit, it does not generate an audit trap, but lower-precedence rules and the role default actions can still specify generating an audit trap for this data packet if there is a match.
- Prohibited — If this rule is hit, no audit trap is generated for this data packet, even when a lower-precedence rule or the role default actions has the Audit Trap action set to enabled.
- Disable Port
- Specify Disable Port functionality for the rule:
- Enabled — If this option is enabled, any port reported as using this rule will be disabled. Ports that have been disabled due to this option are displayed in the device Role/Rule tab.
- Disabled — If this option is disabled and this rule is hit, it does not disable the port, but lower-precedence rules and the role default actions can still specify disabling the port for this data packet if there is a match.
- Prohibited — If this rule is hit, the port is not disabled, even when a lower-precedence rule or the role default actions has the Disable Port action set to enabled.
- Traffic Mirror
- Specify traffic mirroring functionality for the rule:
- Select port group(s) — Use the drop-down list to specify the port groups where mirrored traffic will be sent for monitoring and analysis. Select View/Modify Port Groups to open the
Port Groups tab where you can define
user-defined port groups for selection.
To the right of the drop-down list is an option to mirror only the first (N) packets of a flow. This option is intended for use when mirroring traffic to an ExtremeAnalytics engine. The ExtremeAnalytics engine only needs the initial packets of a flow to properly identify the traffic, and setting this option will reduce network traffic overhead for the switch and engine. By default this number is set to 10, but can be changed by selecting the Edit button . Note that the value you set is used by all mirror actions in use in the current domain.
. Note that the value you set is used by all mirror actions in use in the current domain. - Disabled — If this option is disabled and this rule is hit, traffic mirroring will not take place, but lower-precedence rules and the role default actions can still specify traffic mirroring for this data packet if there is a match.
- Prohibited — If this rule is hit, traffic mirroring is disabled, even when a lower-precedence rule or the role default actions has the Traffic Mirror action specified.
- Select port group(s) — Use the drop-down list to specify the port groups where mirrored traffic will be sent for monitoring and analysis. Select View/Modify Port Groups to open the
Port Groups tab where you can define
user-defined port groups for selection.
- Quarantine Role
- Specify the Quarantine Role functionality for the rule:
- Select Role — Use the drop-down list to select the role that you want to assign as a Quarantine role. Specifying a role as a Quarantine role turns the role's icon red, denoting its restrictive nature.
- Disabled — If this option is disabled and this rule is hit, a Quarantine role will not be assigned, but lower-precedence rules can still specify a Quarantine role for this data packet if there is a match.
- Prohibited — If this rule is hit, a Quarantine role will not be assigned, even when a lower-precedence rule has a Quarantine role action specified.
- Select Role — Use the drop-down list to select the role that you want to assign as a Quarantine role. Specifying a role as a Quarantine role turns the role's icon red, denoting its restrictive nature.
For information on related help topics: