Use this window to add switches to a gateway engine or
engine group. The window allows you to select one or more switches from the
device tree, and set the primary and secondary ExtremeControl Gateways for the
switches. It also lets you set other parameters including the authentication access type for the switches
and the RADIUS attributes to send.
| NOTE: | If desired, you can set only the primary ExtremeControl Gateway for the switches; ExtremeCloud IQ Site Engine does not require the secondary ExtremeControl Gateway to be set.
If only the primary ExtremeControl Gateway is set, then by default that gateway uses its primary
proxy RADIUS server as a secondary direct RADIUS server to the switch.
This allows for redundancy without the requirement for a secondary ExtremeControl Gateway.
In this
scenario, if contact with the ExtremeControl Gateway fails, authentication traffic would bypass
the ExtremeControl gateway, but normal authentication would continue in the network, and still provide some security.
|
|---|
You can access this window by selecting an engine or engine group and selecting the Add Switch button in the right-panel Switches tab.
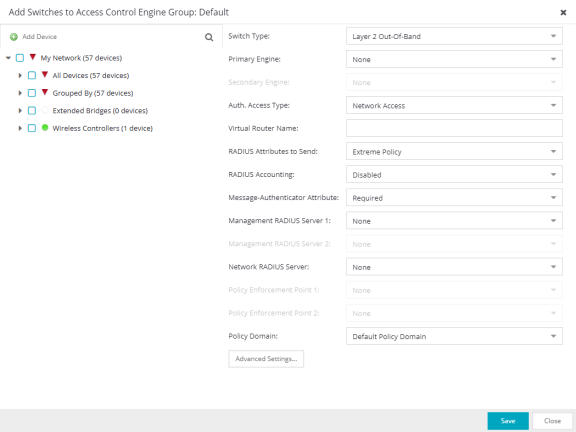
- Device Tree
- This area displays the device tree. Expand the tree and select the switches you want to add to the engine or engine group.
- Add Device
- Opens the Add Device window where you can add a device to the ExtremeCloud IQ Site Engine database. The device is displayed in the My Network folder in the device tree.
- Switch Type
- Use the drop-down list to select the type of switch you are adding:
- Layer 2 Out-Of-Band — A switch that authenticates on layer 2 traffic via RADIUS to an out-of-band ExtremeControl gateway.
- Layer 2 Out-Of-Band Data Center — A switch within a data center where virtualization and mobility are a factor. If an end-system changes location but does not move to a different ExtremeControl engine, ExtremeControl removes the end-system authentication from their prior port/switch. This allows VMs that quickly move from one server to another and then back again to still have their location updated in ExtremeCloud IQ Site Engine, because only one authenticated session is allowed per end-system in ExtremeCloud IQ Site Engine.
- Layer 2 RADIUS Only — In this mode, ExtremeCloud IQ Site Engine does not require any information from the switch other than the end-system MAC address (from Calling-Station-Id or User-Name). The NAS-Port does not need to be specified. If the switch supports RFC 3576, you can set the Reauthentication Behavior in the Advanced Switch Settings window. IP resolution and reauthentication might not work in this mode.
- VPN - A VPN concentrator being used in an ExtremeControl VPN deployment. In this case, you should specify one or more Policy Enforcement Points below. If you do not specify a Policy Enforcement Point, then ExtremeCloud IQ Site Engine is unable to apply policies to restrict access after the user is granted access.
- Primary Gateway
- Use the drop-down list to select the primary ExtremeControl Gateway for the selected switches. If load balancing has been configured for the engine group, the ExtremeCloud IQ Site Engine server determines the primary and secondary gateways at Enforce, and this field displays Determined by Load Balancer.
- Secondary Gateway
- Use the drop-down list to select the secondary ExtremeControl Gateway for the selected
switches. If load balancing has been configured for the engine group, the ExtremeCloud IQ Site Engine server determines the primary and secondary gateways at Enforce, and this field displays Determined by Load Balancer.
NOTE: To configure additional redundant ExtremeControl Gateways per switch (up to four), use the Display Counts option in the Display options panel (Administration > Options > ExtremeControl).
- Auth. Access Type
- Use the drop-down list to select the type of authentication access allowed for these
switches. This feature allows you to have one set of switches for authenticating
management access requests and a different set for authenticating
network access requests.
WARNING: ExtremeControl uses CLI access to perform configuration operations on VOSS/Fabric Engine devices. ExtremeControl uses SNMP and CLI access to perform configuration operations on EXOS/Switch Engine devices based on the firmware version. - Enabling an Auth type of "Any Access" or "Management Access" can restrict access to the switch after an enforce is performed. Make sure that an appropriate administrative access configuration is in place by assigning a profile such as "Administrator ExtremeControl Profile" to grant proper access to users. Also, verify that the current switch CLI credentials for the admin user are defined in the database that ExtremeCloud IQ Site Engine authenticates management login attempts against.
- Switching from an Auth type of "Any Access" or "Management Access" back to "Network Access" can restrict access to the switch after an enforce is performed. Verify that the current switch CLI credentials for the admin user are defined locally on the switch.
- Any Access - the switch can authenticate users originating from any access type.
- Management Access - the switch can only authenticate users that have requested management access via the console, Telnet, SSH, or HTTP, etc.
- Network Access - the switch can only authenticate users that are accessing the network via the following authentication types: MAC, PAP, CHAP, and 802.1X. If RADIUS accounting is enabled, then the switch also monitors Auto Tracking, CEP (Convergence End Point), and Switch Quarantine sessions. If there are multiple sessions for a single end-system, the session with the highest precedence displays to provide the most accurate access control information for the user. The ExtremeControl authentication type precedence from highest to lowest is: Switch Quarantine, 802.1X, CHAP, PAP, Kerberos, MAC, CEP, RADIUS Snooping, Auto Tracking.
- Monitoring - RADIUS Accounting - the switch monitors Auto Tracking, CEP (Convergence End Point), and Switch Quarantine sessions. ExtremeCloud IQ Site Engine learns about these session via RADIUS accounting. This allows ExtremeCloud IQ Site Engine to be in a listen mode, and to display access control, location information, and identity information for end-systems without enabling authentication on the switch. If there are multiple sessions for a single end-system, the session with the highest precedence displays to provide the most accurate access control information for the user. The ExtremeControl authentication type precedence from highest to lowest is: Switch Quarantine, 802.1X, CHAP, PAP, Kerberos, MAC, CEP, RADIUS Snooping, Auto Tracking.
- Manual RADIUS Configuration - ExtremeCloud IQ Site Engine does not perform any RADIUS configurations on the switch. Select this option if you want to configure the switch manually using the Policy tab or CLI.
- Virtual Router Name
- Enter the name of the Virtual Router. The default value for this field is VR-Default.
WARNING: For ExtremeXOS/Switch Engine devices only. If ExtremeCloud IQ Site Engine has not detected and populated this field, enter the Virtual Router Name carefully. Incorrectly entering a value in this field causes the RADIUS configuration to fail, which is not reported when enforcing the configuration to the switch.
- Gateway RADIUS Attributes to Send
- Use the drop-down list to select the RADIUS attributes included as part of the RADIUS response from the ExtremeControl engine to the switch. You can also select New or Manage from the menu to open the RADIUS Attribute Settings window where you can define, edit, or delete the available attributes.
- RADIUS Accounting
- Use the drop-down list to enable RADIUS accounting on the switch. RADIUS accounting can be used to determine the connection state of the end-system sessions on the ExtremeControl engine, providing real-time connection status in ExtremeCloud IQ Site Engine.
- Message-Authenticator Attribute
- Defines if the Access-Request must contain the Message-Authenticator attribute in the RADIUS communication with this device. Not every RADIUS client supports this attribute, but the security best practice is to require the Message-Authenticator attribute.
- Management RADIUS Server 1 and 2
- Use the drop-down list to specify RADIUS servers used to authenticate requests for administrative access to the selected switches. Select from the RADIUS servers you have configured in ExtremeCloud IQ Site Engine, or select New or Manage RADIUS Servers to open the Add/Edit RADIUS Server or Manage RADIUS Servers windows.
- Network RADIUS Server
- This option lets you specify a backup RADIUS server to use for network authentication requests for the selected switches. This allows you to explicitly configure a network RADIUS server to use if there is only one ExtremeControl engine. (This option is only available if a Secondary Gateway is not specified.) Select from the RADIUS servers you have configured in ExtremeCloud IQ Site Engine, or select New or Manage RADIUS Servers to open the Add/Edit RADIUS Server or Manage RADIUS Servers windows.
- Policy Enforcement Point 1 and 2
- Select the Policy Enforcement Points used to provide
authorization for the end-systems connecting to the VPN device you are
adding. The list is populated from the N-Series, S-Series, and K-Series devices in your
Console device tree. If you do not specify a Policy Enforcement Point, then ExtremeControl
is unable to apply policies to restrict end user access after the user is
granted access.
- Policy Domain
- Use this option to assign the switch to a policy domain and enforce the domain configuration to
the switch. The switch must be an Extreme Networks switch.
- Advanced Settings
- Select the Advanced Settings button to open the Advanced Switch Settings window.
For information on related help topics: