Selecting Access Control in the left panel of the Options tab provides the following view, where you can edit settings associated with the Control > Access Control tab. The right-panel view changes depending on what you select in the left-panel tree. Expand the Access Control tree to view all the different available options. These settings apply to all users.
Changing a value from the system default causes a Default Value button to appear. Selecting this button changes the field back to the system default value.
Select the link for information on the following ExtremeControl options:
- Advanced
- Assessment Server
- Data Persistence
- Display
- End-System Event Cache
- Enforce Warning Settings
- Features
- Notification Engine
- Policy Defaults
- Status Polling and Timeout
Advanced
Use this view to configure advanced settings for the Access Control tab.
- Enable IPv6 Addresses for End-Systems
- The Enable IPv6 Addresses for End-Systems option enables ExtremeControl
to collect, report, and display IPv6 addresses for end-systems in the
end-systems table. When this option is changed, you must enforce your
engines before the new settings take effect. In addition,
end-systems need to rediscover their IP addresses in order to
reflect the change in the end-systems table. This can be done by either
deleting the end-system or performing a Force Reauth on the end-system.
Only end-systems with a valid IPv4 address as well as one or more IPv6 addresses are supported. End-systems with only IPv6 addresses are not supported. End-system functionality support varies for IPv6 end-systems. For complete information, see IPv6 Support in the ExtremeCloud IQ Site Engine Configuration Considerations Help topic.
- Resource Allocation Capacity
- The Resource Allocation Capacity option lets you configure the ExtremeCloud IQ Site Engine resources allocated to end-system and configuration processing services. The greater the number of
end-systems and engines in your ExtremeControl deployment, the more resources
it requires.
- Low - For low performance shared systems.
- Low-Medium - For medium performance shared systems, or low performance dedicated systems
- Medium - For medium performance shared systems, or medium performance dedicated systems.
- Medium-High - For high performance shared systems, or medium performance dedicated systems.
- High - For high performance dedicated systems.
- Maximum - For extremely high performance dedicated systems.
- Hybrid Mode
- A Layer 2 ExtremeControl Controller engine can be configured for Hybrid Mode which enables it to act as a RADIUS proxy for switches, like an ExtremeControl Gateway engine. Select this option to enable Hybrid Mode for your Layer 2 Controllers at a global level. Disabling Hybrid Mode at the global level when switches are assigned to a controller is similar to deleting a gateway: the controller is removed from the switches as a reference.
Assessment Server
- ExtremeControl Assessment Web Update Server
- Displays the web update server used by ExtremeControl to update ExtremeControl assessment server software. This update operation pertains only to ExtremeControl on-board agent-less assessment servers.
Use these options to provide assessment agent adapter credentials.
- Assessment Agent Adapter Credentials
- Specify the username and password the ExtremeControl engine uses when attempting to connect to network assessment servers, including Extreme Networks Agent-less, Nessus, or a third-party assessment server (an assessment server not supplied or supported by ExtremeCloud IQ Site Engine). The password is used by the assessment agent adapter (installed on the assessment server) to authenticate assessment server requests. ExtremeCloud IQ Site Engine provides a default password you can change, if desired. However, if you change the password here, you need to change the password on the assessment agent adapter as well, or connection between the engine and assessment agent adapter is lost and assessments are not performed. For additional information, see How to Change the Assessment Agent Adapter Password.
Data Persistence
Use this panel to customize how ExtremeControl ages-out or deletes end-systems, end-system events, and end-system health (assessment) results from the tables and charts in the End-Systems tab.
Daily Persistence
- Run Data Persistence Checks Each Day At
- Set the time that the Data Persistence Check is performed each day.
Age End-Systems
- Age End-Systems Older Than
- Specify the amount of time ExtremeCloud IQ Site Engine keeps end-system information in the database. Each day, when the Data Persistence check runs, it searches the database for
end-systems for which ExtremeControl did not receive an event in the number of days
specified (90 days by default). It removes those end-systems from the
End-System table in the
End-Systems tab.
If you select the Remove Associated MAC Locks and Occurrences in Groups checkbox, the aging check also removes any MAC locks or group memberships associated with the end-systems being removed.
The Remove Associated Registration Data checkbox is selected by default, so that the aging check also removes any registration data associated with the end-systems being removed.
End-System Events
- Age End-System Events Older Than
- End-system events are stored in the database. Each day, when the Data Persistence check runs, it removes all end-system events which are older than the number of days specified (90 days by default).
- Persist Non-Critical End-System Events
- Select this checkbox to save non-critical end-system events (e.g. duplicate end-system events, re-authentication events where the end-system's state did not change) to the database.
Transient End-Systems
- Delete Rejected End-Systems
- Select this checkbox to delete end-systems in the Rejected state as part of the cleanup.
- Delete Transient End-Systems Older Than
- Specify the amount of time to keep transient end-systems in the database before they are deleted as part of the nightly database cleanup task. The default value is 1 day. A value of 0 disables the deletion of transient end-systems. Transient end-systems are unregistered end-systems not seen for the specified number of days. End-systems are not deleted if they are part of an End-System group or there are MAC locks associated with them.
End-System Information Events
- Generate ExtremeControl Events When End-System Information is Modified
- Select the checkbox if you want ExtremeControl to generate an event when end-system information is modified.
Health Results
- Only Persist Health Result Details for Quarantined End-Systems (with the exception of agent-based results)
- Select this checkbox to only save the health result details for quarantined end-systems (with the exception of agent-based health result details, which are always saved for all end-systems).
- Persist Duplicate Health Result Summary and Details
- Select this checkbox to save duplicate health result summaries and details. By default, duplicate health results obtained during a single scan interval are not saved. For example, if the assessment interval is one week, and an end-system is scanned five times during the week with identical assessment results each time, the duplicate health results are not saved (with the exception of administrative scan requests such as Force Reauth and Scan, which are always saved). This reduces the number of health results saved to the database.
- Save a Health Result Summary for the Last N Health Results per End-System
- Specify how many health (assessment) result summaries are saved and displayed in the End-Systems tab for each end-system. By default, the Data Persistence check saves the last 30 health result summaries for each end-system.
- Save the Details for the Last N Health Results per End-System
- Specify how many health (assessment) result details are saved and displayed in the End-Systems tab for each end-system. By default, the Data Persistence check saves detailed information for the last five health results per end-system.
Wireless End-System Events
- Process and Include Wireless End-System Events in End-System Event Logs
- Select the checkbox if you want ExtremeCloud IQ Site Engine to generate an event when wireless end-system information is modified. This option is disabled by default.
Display
Use this Options view to configure new column names for the Custom columns in the End-System table on the Control > End-Systems tab, as well as the number of redundant ExtremeControl Gateways you can select when adding or editing a switch in an ExtremeControl Engine group.
- Custom End-System Information Labels
- This option lets you specify new text for the Custom column headings in the End-System table on the End-Systems tab.
- Displayed ExtremeControl Engines per Switch
- Select the number of ExtremeControl engines displayed in the Add Switches to Group or Edit Switches in Group windows. By default, these windows enable you to configure two ExtremeControl engines per switch for redundancy, but this option enables you to increase the number up to three or four engines per switch.
End-System Event Cache
End-system events are stored in the database. In addition, the end-system event cache stores the most recent end-system events in memory and displays them in the End-System Events tab. This cache enables ExtremeControl to quickly retrieve and display end-system events without having to search through the database.
Use these options to configure the amount of resources used by the end-system event cache.
- Maximum Time to Spend Searching for Events
- Specify the time ExtremeCloud IQ Site Engine spends when searching for older events outside of the cache. (The search is initiated by using the Search for Older Events button in the End-System Events tab.) The search is ended when the number of seconds entered is reached.
- Number of Events to Cache
- Specify the number of events to cache. The more events you cache, the faster data is returned, but caching uses more memory.
- Number of MACs in Secondary Cache
- The End-System Event Cache also keeps a secondary cache of events by MAC address. This means that a particular end-system's events can be more quickly accessed in subsequent requests. Use this field to specify the number of MAC addresses kept in the secondary cache. Keep in mind that the more MAC addresses you cache, the more memory used. Also, note that the secondary cache can include events not in the main cache.
Enforce Warnings to Ignore
Select the checkbox next to the warning message you don't want displayed and select Save.
When an engine configuration audit is performed during an Enforce operation, warning messages can display in the audit results listed in the Enforce window. If there is a warning associated with an engine, you are given the option to acknowledge the warning and proceed with the enforce anyway.
Use these settings to select specific warning messages you do not want displayed in the audit results. This enables you to proceed with the Enforce without having to acknowledge the warning message. For example, your network always results in one of these warning messages on your ExtremeControl configuration. By selecting that warning here, it is ignored in future audit results and you no longer need to acknowledge it before proceeding with the Enforce.
Features
Use this panel to automatically create new Policy mappings and profiles. If you are not using these features, disable them to remove sections that pertain only to those features from certain ExtremeControl windows.

Intune Compliance Module
Use this panel to configure integration with Microsoft Intune and Defender to handle non-compliant end systems. The Site Engine periodically downloads the list of non-compliant Intune IDs through API calls from Microsoft. The Intune ID is a unique identifier of a device enrolled into Microsoft Intune. The entries of the list are compared with the content of end-systems Certificate URI and if the non-compliant end-system is found then the MAC address of such end-system is added to End-System Group for Non-compliant Devices.
- Enable Compliance Check
- Enable or disable the compliance integration with Microsoft Intune.
- Check Interval
- Defines how often ExtremeCloud IQ Site Engine downloads the list of non-compliant Intune IDs from Microsoft.
- Intune Configuration
- Defines how to access the Microsoft Intune API. The mandatory fields are:
- Client ID
- The application identifier of the registered application in Entra ID. In Entra ID the App ID is the Application (client) ID.
- Client Secret
- The client secret for the registered application in Entra ID.
- Scope
- The scope used by API calls.
- Token Endpoint
- The OAuth 2.0 token endpoint (v2) provided by Entra ID in App registrations.
- Non-compliant Behavior
- Defines what happens with non-compliant end-systems reported by Microsoft Intune
- End-System Group for Non-compliant Devices
- Defines a MAC based end-system group where the MAC address of a Non-compliant device is added.
Notification Engine
Use this panel to define the default content contained in ExtremeControl notification action messages. For example, with an email notification action, define the information contained in the email subject line and body. With a syslog or trap notification action, define the information included in the syslog or trap message.
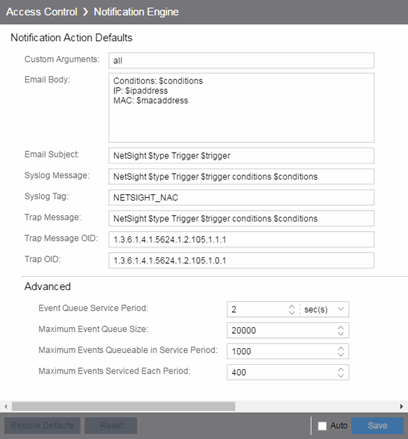
There are certain "keywords" available to use in your email, syslog, and trap messages to provide specific information. Following is a list of the most common keywords used. For additional information, see Keywords.
- $type - the notification type.
- $trigger - the notification trigger.
- $conditions - a list of the conditions specified in the notification action.
- $ipaddress - the IP address of the end-system that is the source of the event.
- $macaddress - the MAC address of the end-system that is the source of the event.
- $switchIP - the IP address of the switch where the end-system connected.
- $switchPort - the port number on the switch where the end-system connected.
- $username - the username provided by the end user upon connection to the network.
- Custom Arguments
- If the notification action specifies a custom program or script to be run on the ExtremeCloud IQ Site Engine Server, then use this field to enter the "all" option. Using the "all" option returns values for all the ExtremeControl Notification keywords applicable to the notification type. For additional information, see Keywords.
- Event Queue Service Period
- Defines how often the queue is checked for events to process. The dispatcher runs one time every service period. So by default, the dispatcher processes events every 5 seconds.
- Maximum Event Queue Size
- The maximum number of events that can be queued. By default, the dispatcher drops events after 5000 events are queued.
- Maximum Events Queuable in Service Period
- This limits the rate that events can be added to the queue (not processed from the queue) and protects the event engine against a large amount of events arriving too quickly. If events arrive at a rate that exceeds this amount, they are discarded.
- Maximum Events Serviced Each Period
- The maximum number of events pulled from the queue for processing each service period. By default, the dispatcher processes 100 events every service period.
Policy Defaults
Use this Options view to specify a default policy for each of the four access policies. These default policies display as the first selection in the drop-down menus when you create an ExtremeControl profile. For example, if you specify an Assessment policy called "New Assessment" as the Policy Default, then "New Assessment" is automatically displayed as the first selection in the Assessment Policy drop-down list in the New ExtremeControl Profile window.
ExtremeCloud IQ Site Engine supplies seven policy names from which you can select. Add more policies in the Edit Policy Mapping window, where you can also define policy to VLAN associations for RFC 3580-enabled switches. After a policy is added, it becomes available for selection in this view.
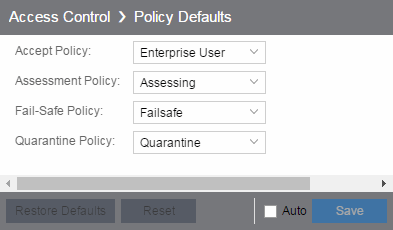
- Accept Policy
- Select the default Accept policy. The Accept policy is applied to an end-system when the end-system is authorized locally by the ExtremeControl engine and passed an assessment (if an assessment was required), or the "Replace RADIUS Attributes with Accept Policy" option is used when authenticating the end-system.
- Assessment Policy
- Select the default Assessment policy. The Assessment policy is applied to an end-system while it is being assessed (scanned).
- Fail-Safe Policy
- Select the default fail-safe policy. The fail-safe policy is applied to an end-system if the end-system's IP address cannot be determined from its MAC address, or if there is a scanning error and an assessment of the end-system could not take place.
- Quarantine Policy
- Select the default Quarantine policy. The Quarantine policy is applied to an end-system if the end-system fails an assessment.
Status Polling and Timeout
Use this Options panel to specify the enforce timeout and status polling options for ExtremeControl engines.
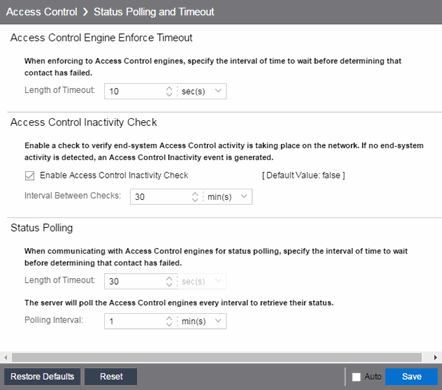
- ExtremeControl Engine Enforce Timeout
- When enforcing to ExtremeControl engines, this value specifies the amount of time ExtremeCloud IQ Site Engine waits for an enforce response from the engine before determining the engine is not responding. During an enforce, an ExtremeControl engine responds every second to report that the enforce operation is either in-progress or complete. Do not increase this timeout value, unless you are experiencing network delays that require a longer timeout value.
- ExtremeControl Inactivity Check
- Enable a check to verify end-system ExtremeControl activity is taking place on the network. If no end-system activity is detected, an ExtremeControl Inactivity event is sent to the Events view. Use the Alarms and Events tab to configure custom alarm criteria based on the ExtremeControl Inactivity event to create an alarm, if desired.
- Status Polling
- Length of Timeout —
When communicating with ExtremeControl engines for status polling, this value specifies the
amount of time ExtremeCloud IQ Site Engine waits before determining
contact failed. If ExtremeCloud IQ Site Engine does not receive a
response from an engine in the defined amount of time, ExtremeCloud IQ Site Engine considers the engine to be "down".
The engine status refers to Messaging connectivity, not SNMP
connectivity. This means that if the engine is "down," ExtremeCloud IQ Site Engine is not able to enforce a new configuration to it.
Polling Interval — Specifies the frequency ExtremeCloud IQ Site Engine polls the ExtremeControl engines to determine engine status.
For information on related help topics: