The AAA Configuration defines the RADIUS and LDAP configurations that provide the authentication and authorization services to your ExtremeControl engines. A AAA Configuration can be a basic or advanced configuration. Basic AAA Configurations define the authentication and authorization services for all end-systems connecting to your ExtremeControl engines Advanced AAA configurations allow you to define different authentication and authorization services for different end users based on end-system to authentication server mappings.
This Help topic provides the following information for accessing and configuring the AAA Configuration:
| NOTE: |
Users with a AAA configuration using NTLM authentication to a back-end active directory domain whose passwords expire are prompted via windows to change their domain password. |
Accessing the AAA Configuration
Use the following steps to edit or change your AAA Configuration.
- Open the Control tab in ExtremeCloud IQ Site Engine.
- Select the Access Control tab.
- Select AAA Configurations within the left-panel tree. The AAA Configuration is displayed in the right panel.
- Use the fields in the right panel to edit or modify the configuration. See the sections below for a description of each field and option in the panel.
- Select Save to save your changes.
Basic AAA Configuration
Basic AAA Configurations define the RADIUS and LDAP configurations for all end-systems connecting to your ExtremeControl engines.
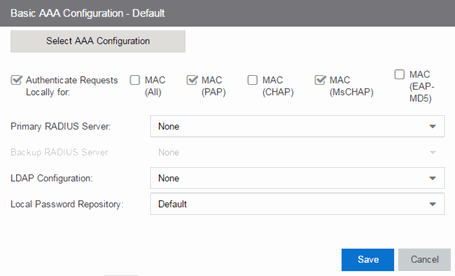
- Authenticate Requests Locally
- This option lets you specify that MAC authentication requests are handled locally by the ExtremeControl engine. Select this option if all MAC
authentication requests are to be authorized, regardless of the MAC
authentication password (except MAC (EAP-MD5) which requires a password
that is the MAC address). The Accept policy is applied to end-systems
that are authorized locally.
Select one or more MAC authentication types:- MAC (All) — includes MAC (PAP), MAC (CHAP), MAC (MsCHAP), and MAC (EAP-MD5) authentication types.
- MAC (PAP) — this is the MAC authentication type used by Extreme Networks wired and wireless devices.
- MAC (CHAP)
- MAC (MsCHAP)
- MAC (EAP-MD5) — this MAC authentication type requires a password, which must be the MAC address.
- Primary/Backup RADIUS Servers
- If your ExtremeControl engines are configured to proxy RADIUS requests to a
RADIUS server, use these fields to specify the primary and backup
RADIUS servers to use.
Use the drop-down list to select a RADIUS server, add or edit a RADIUS server, or
manage your RADIUS servers.
- LDAP Configuration
- Use this field to specify the LDAP configuration for the LDAP
server on your network that you want to use in this AAA configuration.
Use the drop-down list to select an LDAP configuration, add or edit an LDAP configuration, or manage your LDAP configurations.
- Local Password Repository
- Use this field to specify the local password repository you want for this AAA configuration. ExtremeCloud IQ Site Engine supplies a default repository to define passwords for administrators and sponsors accessing the Registration administration web page and the sponsor administration web page. The default password is Extreme@pp. Use the drop-down list to select a repository.
Advanced AAA Configuration
Advanced AAA configurations allow you to define different authentication and authorization services for different end users based on end-system to authentication server mappings. Mappings can be based on:
- authentication type
- username/user group
- MAC address/end-system group
- hostname/hostname group
- location group
- authentication method
- RADIUS user group
- LDAP user group
| NOTE: | LDAP User Group is only available with an Authentication Type of Registration. |
For example, in a higher education setting, you may want faculty members authenticating to one RADIUS server and students authenticating to another. You can also create mappings specifically for authenticating management login requests, when an administrator logs into a switch's CLI via the console connection, SSH, or Telnet.
Mappings are listed in order of precedence from the top down. If an
end-system does not match any of the listed mappings, the RADIUS request is
dropped. Because of this, you might want to use the "Any" mapping (created automatically when you add a new advanced AAA configuration) as your
last mapping in the list.
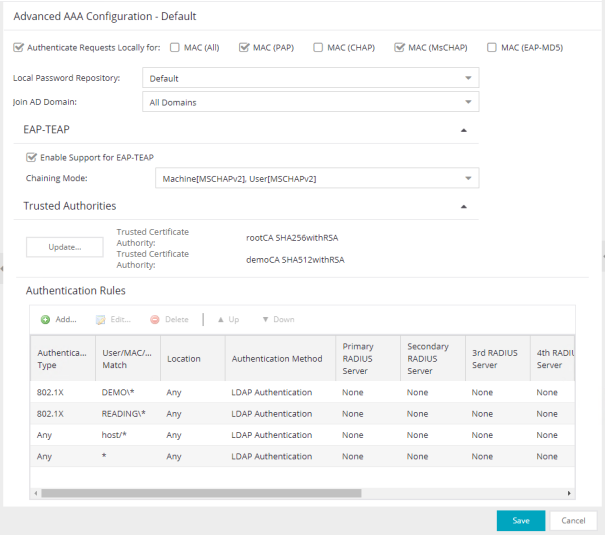
- Authenticate Requests Locally for
- This option lets you specify that MAC authentication requests are handled locally by the ExtremeControl engine. Select this option if all MAC
authentication requests are to be authorized, regardless of the MAC
authentication password (except MAC (EAP-MD5) which requires a password
that is the MAC address). The Accept policy is applied to end-systems
authorized locally.
Use the drop-down list to specify a particular type of MAC authentication:- MAC (All) - includes MAC (PAP), MAC (CHAP), and MAC (EAP-MD5) authentication types.
- MAC (PAP) - this is the MAC authentication type used by Extreme Networks wired and wireless devices.
- MAC (CHAP)
- MAC (MsCHAP)
- MAC (EAP-MD5) - this MAC authentication type requires a password, and the password must be the MAC address.
- Local Password Repository
- Use this field to specify the local password repository you want for this AAA configuration. ExtremeCloud IQ Site Engine supplies a default repository that can be used to define passwords for administrators and sponsors accessing the Registration administration web page and the sponsor administration web page. The default password is Extreme@pp. Use the drop-down list to select a repository.
- Join AD Domain
- Use the drop-down list to explicitly select which LDAP configuration of the Active Directory domain the ExtremeControl engine joins in order to authenticate users to all Active Directory domains configured for that engine or select Auto Detect to let the ExtremeControl engine determine the domain. Auto Detect starts at the first entry set to LDAP Authentication in the table and attempt to join that domain. If it cannot join that domain, it goes to the next entry set to LDAP Authentication and attempt to join that domain, and so on until one succeeds.
You can also join multiple Active Directory domains by selecting All Domains and configuring multiple authentication rules with an Authentication Method of LDAP Authentication in the Advanced AAA Configuration tab.NOTE: There are configuration considerations when joining multiple Active Directory Domains.
- Enable Support for EAP-TEAP
- Use this option to enable or disable support for the standard-based chaining protocol EAP-TEAP.
- Chaining Mode
- Use the drop-down list to specify what method to use for Machine authentication and for User authentication. Machine authentication must be first (primary) and User authentication must follow (secondary):
- Machine[MSCHAPv2], User[MSCHAPv2] -The primary authentication uses MSCHAPv2 to authenticate the computer. The secondary authentication uses MSCHAPv2 to authenticate the user.
- Machine[MSCHAPv2], User[TLS] -The primary authentication uses MSCHAPv2 to authenticate the computer. The secondary authentication uses TLS to authenticate the user.
- Machine[TLS], User[MSCHAPv2] -The primary authentication uses TLS to authenticate the computer. The secondary authentication uses MSCHAPv2 to authenticate the user.
- Machine[TLS], User[TLS] -The primary authentication uses TLS to authenticate the computer. The secondary authentication uses TLS to authenticate the user.
- Trusted Authorities
- Configure the AAA Trusted Certificate Authorities to designate which client certificates can be trusted. For more information see, How to Configure Local RADIUS Termination at the ExtremeControl Engine
- Use the Update... button to update the AAA trusted Certificate Authorities for your AAA configuration:
-
- Provide one or more CA certificates for Certificate Authorities that are trusted to issue client certificates for 802.1X authentication. Client certificate issued by an untrusted Certificate Authority are not accepted and the authentication session will be rejected.
-
Optionally, provide one or more URLs for Certificate Revocation Lists (CRLs), or Online Certificate Status Protocol (OCSP) configuration to check for revoked certificates. You must provide one for every used Certificate Authority, or none.
- CRL
- Use this option to define the URLs where the Certificate Revocation List can be downloaded.
- Allow expired CRLs to be used when checking CRLs - Defines the system behavior if the CRL is expired.
- Allow CRLs to be missed when checking CRLs - Defines the system behavior if the CRL is missing.
- OCSP
- Use this option to configure the Online Certificate Status Protocol to check for revoked certificates. Access Control Engine validates the client certificate during authentication by sending requests to the OCSP responder. The OCSP responder URL can be configured manually or obtained from the client certificate.
- Always Override Certificate URL with Default Responder URL - Defines if the OCSP Responder URL is used regardless of the potential URL in the certificate.
Default Responder URL - Defines that the Default Responder URL is used if the certificate does not contain the URL, or the Always Override Certificate URL with Default Responder URL is checked.- Secondary Responder URL - If defined, the Access Control Engine periodically checks the reachability of the Default responder. The Secondary responder is used If the Default responder is not reachable. Once the Default responder is back in service and reachable, the Default responder is used again. OCSP Responder Health Check is configured in Access Control > Configuration > Global & Engine Settings > Engine Settings > Miscellaneous.
Responder URL Timeout - Defines the timeout for the Responder URL, in seconds.
Verify Nonces Uniqueness - Defines if the nonce value must be unique.
Continue Processing Requests After Responder Error - Defines the system behavior if a responder error occurs. If checked and the responder returns an error the authentication continues to be processed. If unchecked and the responder returns an error the authentication is rejected.
- Authentication Rules
- This table lists mappings between groups of users and authentication configurations. The table displays the username to match along with the defined configuration parameters for that mapping. Mappings are listed in order of precedence from the top down. If an end-system does not match any of the listed mappings, the RADIUS request is dropped. Because of this, you might want to use an "Any" mapping as your last mapping in the list. Use the Mappings toolbar buttons to perform actions on the mappings.
-
 Move
Mappings Up/Down
Move
Mappings Up/Down
- Move mappings up and down in the list to determine mapping precedence. Mappings are listed in order of precedence from the top down.
-
 Add New
Mapping
Add New
Mapping
- Opens the Add User to Authentication Mapping window where you can define a new mapping.
-
 Edit
Mapping
Edit
Mapping
- Opens the Edit User to Authentication Mapping window where you can edit the selected mapping.
For information on related help topics: